Rabbit Ransomware Removal Guide
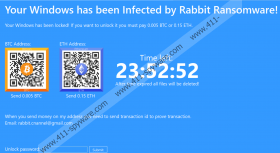
Rabbit Ransomware blocks the screen and demands victims to pay for unblocking it in 24 hours. The victims have two options either to pay in BTC or ETH. No matter which cryptocurrency one chooses, the sum should be more or less the same, which is approximately 24 US dollars at the moment of writing. Of course, we do not advise paying it as it is entirely unnecessary. We may have a password that could unlock the screen and if that does not work, removing the malicious application will do the job. You can find more information about this screen locker in the rest of the article. What's more, to make the removal task a bit easier, our researchers have prepared instructions explaining how to get rid of Rabbit Ransomware manually. You can find these steps at the end of this report.
First of all, it is important to explain where threats like Rabbit Ransomware could come from. In this case, it looks like the malware could be spread with fake system updates as the launcher we came across was called Windows Driver Update.exe. However, such malicious applications can be spread with various software installers or infected email attachments too. Thus, if you wish to keep your computer clean and protected, you should be cautious with all data downloaded/received from the Internet. Especially, if such data comes from P2P file sharing web pages and websites alike. If you are unsure whether the data you obtain is trustworthy or not, we recommend scanning it with a chosen security tool. This you should do before opening the file in question as once it is launched it could be already too late to do anything.
Furthermore, if the malware’s launcher is opened, the threat ought to create a couple of Registry files to settle in. The first one should be a value name called Windows_Service in the HKCU\Software\Microsoft\Windows\CurrentVersion\Run location. This particular data should make the device relaunch Rabbit Ransomware when it restarts. The other value name is supposed to be called DisableTaskMgr, and it should be located in the HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System directory. With it, the malicious application can block the user’s Task Manager and so make it more difficult to get rid of it. Soon after creating this data, the malware should lock the screen by covering it up with a blue window containing instructions. They explain how to make the payment, contact the hackers behind Rabbit Ransomware, and get a password that would unlock the screen. Our specialists say the password of the variant they tested is RabbCompany66.
To get rid of the malicious application, you could either try inserting the mentioned password (RabbCompany66) or restart the computer in Safe Mode. For users who wish to continue deleting Rabbit Ransomware manually, we would advise completing the second part of instructions. However, if you prefer using automatic features, you could unblock the screen either way and then install a reliable antimalware tool instead of following the second part of the provided steps. Scan the device with your chosen security tool and press the deletion button that the tool should display the moment the scanning is over.
Restart the device in Safe Mode with Networking
Windows 8 and Windows 10
- Tap Win+I or navigate to the Start menu and click the Power button.
- Tap and hold Shift and click Restart.
- Select Troubleshoot and choose Advanced Options.
- Pick Startup Settings and press Restart.
- Click the F5 key and reboot the system.
Windows XP/Windows Vista/Windows 7
- Open Start, press Shutdown options and tap Restart.
- Press and hold the F8 key when your computer is restarting.
- Wait till you see the Advanced Boot Options window.
- Choose Safe Mode with Networking.
- Press Enter and log on to your computer.
Get rid of Rabbit Ransomware
- Tap Win+E.
- Locate the following directories:
%TEMP%
%USERPROFILE%\Desktop
%USERPROFILE%\Downloads - Find a malicious file downloaded before the malware appeared.
- Right-click the doubtful file and select Delete.
- Press Win+R, type Regedit and click OK.
- Navigate to this directory: HKCU\Software\Microsoft\Windows\CurrentVersion\Run
- Find a value name titled Windows_Service, right-click it and press Delete.
- Go to: HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System
- Locate a value name called DisableTaskMgr, right-click them and press Delete.
- Leave Registry Editor.
- Empty Recycle bin.
- Reboot the device.
Rabbit Ransomware Screenshots: