GoldenAxe Ransomware Removal Guide
GoldenAxe Ransomware is a real danger to your personal files. If it successfully invades your operating system, your files do not stand a chance as the infection can encrypt them using special encryption algorithms. According to our research team, the attacker behind this threat is using the combination of RSA and AES keys to corrupt files and lock the decryption key, which creates one messy situation. If your files were encrypted, they are lost, and you can go back to normal only if backups for the encrypted files exist. If that is the case, once you delete GoldenAxe Ransomware from your browser, you should have no trouble replacing the corrupted photos, documents, and other kinds of files with backups. Without a doubt, you should do this only after you remove the malicious infection. If you need to check if backups exist on virtual clouds or on external drives, find a malware-free computer to do so.
When GoldenAxe Ransomware encrypts your personal files, this malicious threat adds five original characters to the corrupted files. The characters should be unique for every victim, and they might look something like “.AB0CD” or “.MA1AM.” Of course, no extension is necessary to figure out which files were corrupted because you will simply be unable to open them. The point of the entire attack is to make your files inaccessible because that might be the only way for the attackers to get what they want, and that, of course, is your money. Before, GoldenAxe Ransomware reveals itself, it can mess with your operating system too. For example, if a system restore point is set, the infection swiftly deletes shadow volume copies to make it impossible to restore the system to a point before the ransomware existed. The threat also can kill and start processes to ensure that antivirus tools, backups systems, and similar tools are stopped. If the infection is successful, it then reveals itself with the help of three unique files. It is notable that after the threat encrypts files and creates its own files, it should delete itself automatically.
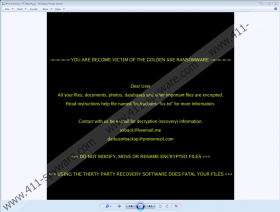
The three files that GoldenAxe Ransomware creates are all used to introduce you to the same message. One file is called “# instructions-[ID] #.jpg,” and it is an image file that might change the Desktop wallpaper or pop-up randomly. The image represents a text message that instructs to read the message in the TXT file as well as to email the attackers. The TXT file is called “# instructions-[ID] #.txt,” and it explains what has happened, reassures that decryption is possible (do not trust this statement), instructs to purchase Bitcoins, and pushes to email xxback@keemail.me and darkusmbackup@protonmail.com for more information. It is suggested that the price of the ransom would be determined based on how fast the victim contacts the attackers. Although that might push you into contacting cyber criminals right away, you need to be smart. Realize that if you email them, they will be able to contact you whenever they want to. The final file is called “# instructions-[ID] #.vbs,” and it is a script file that plays this audio message: “All your files are encrypted. Read the Help file for solution.”
If you pay the ransom requested by the attackers behind GoldenAxe Ransomware, it is guaranteed that you will lose your money. Unfortunately, there are no guarantees when it comes to the decryption of your files. While there is a small chance that your files could be decrypted, we would be very surprised if that was how things went. Most likely, the attackers would simply stop communicating with you once they got the money. This is why we believe that the only logical thing you can do is remove GoldenAxe Ransomware. Sure, your files will not be restored, but you will not lose your money, and your operating system will no longer be in the claws of attackers. Although the threat should remove itself after execution, you must scan your system to be sure of that. Better yet, install anti-malware software that will simultaneously remove all malicious files and will strengthen the security of your operating system.
How to delete GoldenAxe Ransomware
- Delete the ransom note files: # instructions-[ID] #.txt, # instructions-[ID] #.vbs, # instructions-[ID] #.jpg.
- Delete all recently downloaded suspicious files (your goal is to find and Delete the launcher file).
- Empty Recycle Bin and perform a full system scan to make sure that your operating system is clean.
N.B. You might not find the launcher file because it should be removed automatically; however, you must scan the system to make sure that threats do not prevail.
GoldenAxe Ransomware Screenshots:
GoldenAxe Ransomware technical info for manual removal:
Files Modified/Created on the system:
| # | File Name | File Size (Bytes) | File Hash |
|---|---|---|---|
| 1 | # instructions-TC5MA #.vbs | 180 bytes | MD5: 4f061a471fe0a032b4774613273bf4b0 |
| 2 | GoldenAxe.exe | 1685520 bytes | MD5: 3520dec68c0a8b28e7cf7b49e90a706e |
| 3 | # instructions-TC5MA #.txt | 4258 bytes | MD5: f25559894a3edaf6283b69f462f81f97 |
| 4 | # instructions-TC5MA #.jpg | 80192 bytes | MD5: 26f25d4e798b539cce28f3e7f13600ec |
Memory Processes Created:
| # | Process Name | Process Filename | Main module size |
|---|---|---|---|
| 1 | GoldenAxe.exe | GoldenAxe.exe | 1685520 bytes |

