Opencode@india.com Ransomware Removal Guide
Opencode@india.com Ransomware not only encrypts images, media files, archives, documents, and other sensitive files but also corrupts the files of downloaded applications. Due to this, you might be unable to use your browsers, media players, and other apps. The purpose of this threat is to make you pay a ransom, which might be extremely big. Unfortunately, as our research has revealed, cracking the cipher of this ransomware is not possible, and even third-party decryptors will not help. Hopefully, a tool capable of decrypting your files will be invented, but, right now, it does not exist. Overall, whether or not you manage to free your files, removing Opencode@india.com Ransomware is something that you have to focus on, and we are here to help.
The first thing we need to discuss regarding Opencode@india.com Ransomware is its entrance. Was this threat launched as you opened a corrupted spam email attachment? If it was, you should know the name and the location of this malicious file. If this threat was installed silently by other threat or if it was installed without your permission along with a software bundle, you might have to remove other threats. If you cannot see malware, run a malware scanner just to make sure that silent, clandestine threats are not running without your notice. Obviously, if they are – delete them instantly. Unsurprisingly, most users stall when it comes to the removal of Opencode@india.com Ransomware because it can take their personal files hostage. The reality is that your files will remain locked regardless of whether or not you delete the ransomware. As long as you record the email addresses and your unique ID number, you will have the chance to communicate with cyber criminals.
Your unique ID number is hidden in the extension that is attached to the encrypted files. This extension is “.id-[ID number].{opencode@india.com}.xtbl”, and it is similar to the extensions that are added by Radxlove7@india.com, Meldonii@india.com, and many other threats that were created using the CrySIS Ransomware engine. All of these threats use the RSA-2048 encryption key, and all of them can take your files hostage until you pay the ransom. Speaking of the ransom, you will be introduced to the sum only when you contact cyber criminals using the provided emails. Paying it is very risky because there is no guarantee that you would get the promised decryptor. In fact, most ransomware victims who pay the ransom end up losing the money and the files because the ransom payment does not work. Obviously, that makes the situation much more complicated because that means that you might have no way of decrypting your valuable personal files.
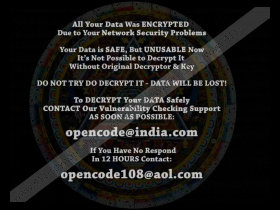
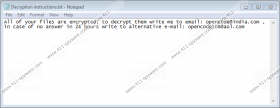
As you know, Opencode@india.com Ransomware can hijack your Desktop wallpaper by replacing it with “Decryption instructions.jpg”. The message within this file is identical to the one represented via "Decryption instructions.txt". This file informs that you have 24 hours to contact the crooks via opencode@india.com or opencode108@aol.com. There is one more file that you might be introduced to, and it is called "READ_DECRYPT DATA INSTRUCTIONS.txt". This ransom note might give you only 12 hours to take action. It is unlikely that there is a time limit at all, but when it comes to devious cyber crooks, you truly never know. We have already warned you that the claims to decrypt your files when you pay the ransom might be false, and so any information that cyber criminals provide you with might be misleading.
Do not be intimidated by the removal guide below. Of course, if you do not feel you are experienced or skilled enough to delete Opencode@india.com Ransomware manually, we recommend utilizing automated malware detection and removal software instead. The download link below represents a free malware scanner; however, this tool can be upgraded to a full-time anti-malware tool. You can rely on it to clean your operating system and keep it guarded in the future. If you need help with any of these removal options, use the comments section below to state your problems, and we will try to resolve them as quickly as possible.
How to remove Opencode@india.com Ransomware
N.B. According to our research, Opencode@india.com Ransomware might be located in one of many directories. This guide shows which directories to check to look for the malicious file. Note that this file might have a unique name in every case.
- Launch Explorer. To launch it, tap Win+E keys simultaneously.
- Enter one of these directories into the address bar and Delete the malicious [unknown].exefile found:
- %ALLUSERSPROFILE%\Start Menu\Programs\Startup\
- %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\
- %USERPROFILE%\Microsoft\Windows\Start Menu\Programs\Startup\
- %ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs\Startup\
- %ALLUSERSPROFILE%\Application Data\Microsoft\Windows\Start Menu\Programs\Startup\
- %WINDIR%\System32\
- %WINDIR%\Syswow64\
- Launch RUN. To launch this dialog box, simultaneously tap Win+R keys.
- Type regedit in the dialog box and press Enter.
- Move to HKCU\Control Panel\Desktop.
- Right-click Wallpaper, select Modify, and clear the value data area.
- Move to HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Wallpapers.
- Right-click BackgroundHistoryPath0, select Modify, and clear the value data area.
- Move to HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run.
- Delete the value with a random name (the value data should point to the location of [unknown].exe file).
Opencode@india.com Ransomware Screenshots: