Nulltica Ransomware Removal Guide
Nulltica Ransomware is a computer infection built using the Hidden Tear platform, which is open-source ransomware created for educational purposes. Many people with minimal skills in coding get the chance to create ransomware which are known to vary in complexity. The Nulltica Ransomware is inactive at the moment due to the unresponsive server. The infection does not encrypt files, but it should be removed from the computer as soon as possible, since the fact that your machine is infected is a sign that you need effective protection from different types of malware.
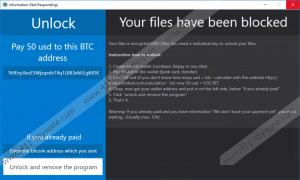
If the Nulltica Ransomware were running properly, it would encrypt files and add the extension .lock. Moreover, the infection would show all the instructions regarding decryption in a program window. Our research shows that the Nulltica threat has some functions typical of keyloggers, which record keyboard input. That means that everything you type in is visible to some cyber crooks, who can use the data obtained for various illegal activities, including identity theft. The Nulltica threat can also be used as a tool to steal Facebook-related information, in which case the stolen information is stored in a .txt file named "log." The code of the infection also shows that the Nulltica threat would be capable of spreading the data obtained through the same Facebook platform. Even though the Nulltica Ransomware does not work as intended, it seems to be created by someone highly interested in obtaining as much personal information as possible. It is crucial to remove the infection so that no other damage is inflicted in the near future.
According to the ransom message, users' data is encoded using the AES 256 algorithm, the name of which refers to the length of the encryption key. This type of encryption is considered one of the most secure encryption methods after 128- and 192-encryption. In order to decrypt files, you are expected to pay a ransom of $50 in Bitcoin, which is approximately 0.02BTC. Bitcoin is a digital currency that is not owned or controlled by any issuer or central bank. Money transactions are made anonymously, allowing cyber criminals to remain unidentified. The warning displayed by the Nulltica Ransomware requires to create a digital Bitcoin wallet and make a money transaction to the wallet given in the same warning. As the infection leaves your files intact, you should not make any money, neither should you ever pay schemers for restoring your files even if they get encrypted. There is no guarantee that someone will bother to decode your files, so you should always be aware of such Internet dangers and make file back-ups to remote devices as often as you can.
Research on the Nulltica Ransomware has also revealed that part of the code of the infection is written in Polish, so it is assumed that threat is a product of some Polish-speaking attackers. Moreover, the whole wording of the ransom warning is quite colloquial and primitive, suggesting that it must have been written by a non-native speaker. Additionally, the Polish Google page Google.pl is mentioned in the code, which adds some weight to our speculation.
The Nulltica Ransomware also has its point of execution (PoE) in the registry. More specifically, it can be accessed by following the path HKCU\Software\Microsoft\Windows\CurrentVersion\Run, where the randomly named registry value created by the infection is stored. Moreover, the infection creates its own copy in the %APPDATA% directory.
Ransomware developers find a variety of ways to spread their malicious products, including popular social networks, emails, software sharing websites, etc. It is highly important that you disregard spam emails or emails sent from questionable senders. Moreover, it is advisable to stay away from websites distributing freeware, the installers of which are very often full of additional programs aimed at deceiving you or obtaining some benefit from you. It is also vital to keep the operating system protected by using a malware and spyware prevention tool which would filter all or part of the Internet you access. If you want to browse the Internet freely, you should consider implementing preventative measures to protect yourself from serious damage.
Below you will find our instructions that will guide you through the removal process. If you find this type of ransomware removal too complex, use our recommended security tool to remove the Nulltica Ransomware from the computer for good.
How to remove the Nulltica Ransomware
- Check your download locations and delete recently downloaded files.
- Press Win+R and type in %APPDATA%.
- Press Enter and delete the file of the infection located in the %AppData% directory.
- Press Win+R and type in regedit. Click OK.
- Follow the path HKCU\Software\Microsoft\Windows\CurrentVersion\Run and delete the entry named randomly and with the value data pointing to the location of the file.
- Clear the Recycle bin.
Nulltica Ransomware Screenshots: