DMA Locker Ransomware Removal Guide
DMA Locker Ransomware is a serious threat, and its creators know what they are doing. According to our research, this infection is on its fourth version, and there is no doubt that it is stronger than ever before. The older versions were also known by the name MadLocker/DMA Ransomware. Whichever name you recognize this infection by, we can assure you that it is malicious. Once installed, it will immediately encrypt your personal files using the combination of AES and RSA encryption algorithms, and, according to our research, it is unlikely that another way to decrypt files exists. Nonetheless, this does not mean that you need to pay the ransom requested by cyber criminals. In fact, this practice is very risky, and it is more likely that you will lose your money than get your files decrypted. Continue reading to learn more about the encryption of files and the removal of DMA Locker Ransomware.
It is difficult to say how DMA Locker Ransomware has entered your operating system, but it is likely that it was executed with a file that you might have downloaded onto your PC yourself. Whether you downloaded it bundled with malware, as a standalone file introduced to you via misleading pop-ups, or as a harmless-looking spam email attachment, this file is responsible for encrypting your files. Our research team has found that, once installed, DMA Locker Ransomware creates a copy of itself (svchosd.exe) in the %ALLUSERSPROFILE% directory. Additionally, this threat will create two files – select.bat and cryptoinfo.txt – to represent the demands of cyber criminals. Luckily, these files are not hidden, and you can locate them momentarily. If you delete svchosd.exe, the remaining files will be responsible for presenting you with the demands of cyber criminals. The main file represents a window that explains the situation and guides you through the payment. The TEXT file carries the same message; however, it is more concise. Here is the message found in the cryptoinfo.txt file.
! ! ! ATTENTION ! ! !
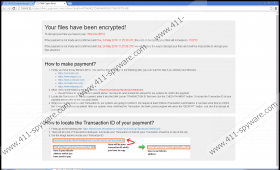
ALL YOUR FILES HAVE BEEN ENCRYPTED!
- IF YOU WANT TO RECOVER YOUR FILES
FOLLOW THE INSTRUCTIONS AT THIS WEBSITE: [web page]
The website that DMA Locker Ransomware presents was set up to help you pay the ransom more quickly. The initial ransom is 1 BTC, which, at the moment, is around 443 USD, but users are threatened with an increase. It is stated that if you do not pay the ransom within 4 days, the ransom will increase to 1.5 BTC (664 USD), and if you do not pay the ransom within the next 4 days, a decryption key will be destroyed. If you trust the information that cyber crooks present, you have 8 days to make the payment, and, after that, you lose your chance to restore them. Although you can open the files that were encrypted by this infection, the data within them is unreadable. For example, if you open a Microsoft Word file that was encrypted, you will see random symbols and characters instead of the original text. Needless to say, if you have not backed up your files (e.g., on an external drive), you might see no other option but to pay the ransom. Well, there is no way of telling if your files will be decrypted if you do. On top of that, you do not want to help out the developers of malware in any way.
If you run anti-malware software, DMA Locker Ransomware removes itself. That is not necessarily a good thing if you are thinking about paying the ransom, because this might take the opportunity away from you. Of course, removing this ransomware is extremely important, and you need to do it as soon as you can. Whether you pay the ransom or not, you have to end your operation by eliminating this threat, and we have created a guide that will help you get rid of this malicious threat. Of course, we also advise implementing reliable anti-malware software because you want to keep your operating system guarded against malicious infections in the future. If you want to ask questions about the removal process, the decryption of files, or anything else, please submit them in the comment box below.
How to delete DMA Locker Ransomware
- Launch Explorer by tapping keys Win+E together.
- Enter %ALLUSERSPROFILE% into the address at the top to access this directory.
- Right-click and Delete these files: svchosd.exe, cryptoinfo.txt, select.bat.
- Launch RUN by tapping Win+R keys together.
- Enter regedit.exe into the Open box to launch Registry Editor.
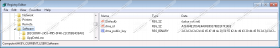
- Navigate to the HKCU\Software path.
- Right-click and Delete these values: dma_id, dma_public_key.
- Navigate to HKCU\Software\Microsoft\Windows\CurrentVersion\Run.
- Right-click and Delete the value called Windows Update (only if the value data points to select.bat).
DMA Locker Ransomware Screenshots: