How to Remove vvv File Extension Removal Guide
If there are files with .vvv extension on your computer, it is a clear indication that your operating system has been attacked by a dangerous Trojan called TeslaCrypt Ransomware. This is an intrusive encryption ransomware that seems to be a copycat of CryptoLocker, an infamous and dangerous malware infection. If your computer has been infected with this Trojan, there is a good chance you can say goodbye to most of your files on your hard drive. As a matter of fact, you cannot really remove TeslaCrypt Ransomware because there is not much really to get rid of. Instead, this worrisome malware leaves you with encrypted and therefore useless files. Once it activates itself and finishes the encryption process, it will warn you about it and ask you to pay a certain amount of money so that you can get the decryption key. Hence the name ransomware. However, we believe that you should not ever think of paying the criminals behind this Trojan. Please continue reading our article to learn more about the threats you have to face if you find this infection on board and how you can protect your computer from similar attacks.
In order to be able to protect your Windows operating system against this encryption ransomware and other similarly dangerous infections, you need to be aware of how these Trojan horses can crawl onto your computer. Although the most effective protection is having a professional security tool that could filter out this threat before it hits your system, you can still be cautious and may be able to avoid this threat. The most likely way for this infection to fool you is via e-mails. No matter how strict spam filter your mail server may have, it is still possible that certain spam e-mails land in your inbox. Some more sophisticated Trojans, for example, can imitate the sender based on your contacts list or simply pose as an official e-mail from a well-known company, such as AOL. Most users would not doubt its credibility and would open the mail.
It is possible that the Trojan gets activated by simply your opening the mail, but most of the time you infect your machine by clicking on the attached file. This could be a simple image or video file. Some Trojans may also use .pdf and .doc files as a disguise. But e-mails are only one major way to get this ransomware onto your computer. What is also very popular nowadays is to infect users via social networking sites. This means that you may see a “must-see” video on your timeline, for instance, in Facebook, but once you click on it, you simply activate the Trojan.
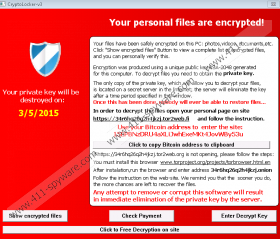
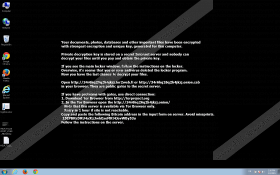
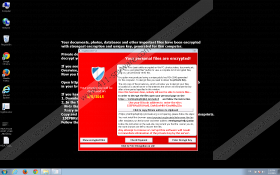
Once this ransomware starts working on your computer, it will encrypt your documents, photos, and databases with the strongest possible encryption method called RSA-2048. When it has finished with all the files, which will have .vvv, .ecc, or .ccc extensions, this TeslaCrypt Ransomware will change your desktop background to a ransom note on black background. In order to make itself surely seen, it also displays a big red pop-up warning with the same message. The main points of this message is that it informs you about the fact of encryption and that the decryption key is stored on a secret server, which you will only get if you pay a certain amount of money in Bitcoin according to the given details.
However, we think that you should refrain from paying any money to these criminals because you have no guarantee that you will get the key and it will really unlock all your files. As a matter of fact, there is only one thing you can do: Learn from this and prevent another attack from destroying your computer. That is why it is so vital to keep a back-up copy of your files on an external hard drive. If you are a security-minded computer user and you do have a back-up copy, all you need to do is run a malware scan on your system and remove all infections. Then, after restarting your computer, you can simply transfer the files from your external drive onto your PC’s hard drive.
You cannot actually remove TeslaCrypt Ransomware once it activates and finishes its “business” because it will simply delete itself. One thing is sure, without the decryption key you will never be able to use your files again. There is no antimalware program that could help you with that. However, you can still clean up the mess this ransomware made and let us not forget about the other possible infections that might also be present on your computer. Therefore, in order to help you protect your computer against further dangers, we recommend SpyHunter as a powerful solution in the malware warfare. Please follow our instructions below so that you can download and install this security tool.
How to remove TeslaCrypt Ransomware
- Start up your browser and enter: http://www.411-spyware.com/download-sph.
- Download and install SpyHunter.
- Run a full system scan and remove all infections.
- Restart your PC.
How to Remove vvv File Extension Screenshots: