Zayka Ransomware Removal Guide
If you find out that Zayka Ransomware has hit your computer, you may have to deal with a great loss as this vicious program can encrypt all your personal files and more to extort money from you for the decryption. Our research has revealed that this new malware threat belongs to a quickly growing ransomware family called CryptoMix. We have seen lately the appearance of Noob Ransomware, Exte Ransomware, and Azer Ransomware, which are all severe hits to your system. Malware specialists have been able to crack some of the variants in this dangerous family, which means that there are free file recovery tools available for download on the web. But, unfortunately, these latest variants are still undecryptable so if you do not have a recent backup of your files, it is possible that you will lose them all in this malicious attack. Although we cannot help you with your encrypted files, we can definitely tell you how you can remove Zayka Ransomware from your computer. Please read our full description about this ransomware program before you scroll down to our instructions.
If this dangerous threat can show up on your computer, it is most likely not protected by an up-to-date security program, which could avert such a malicious attack automatically before it could sneak onto your system. Unfortunately, in most cases it is the victim who lets this beast loose on the computer. One of the main distribution methods for this ransomware is spamming campaigns. Have you opened any doubtful e-mails recently and viewed its attachment? This could be the reason why your files have been encrypted by this ransomware. This spam can be very misleading and convincing because it uses seemingly legitimate senders as well as urgent-looking subjects, including alleged problems with a hotel room booking, changes regarding your Internet provider’s services, unpaid invoices, and more. These are not the kind of matters that you can simply ignore. This is why these crooks know that there will be a lot of unsuspecting users who will fall for this trick. The most important thing to remember about such a ransomware attack is that by the time you realize its presence, it will be too late to delete Zayka Ransomware to stop the encryption and its devastating aftermath.
Apart from becoming more careful around your e-mails, it is also important for you to update your browsers and drivers because cyber crooks can also attack you through malicious pages equipped with Exploit Kits. Such kits like RIG and Angler can exploit security bugs of outdated software versions. Once your browser loads such a page, a malicious script is triggered and drops the infection right away. You can usually get redirected to such a page when your computer is infected with adware or when you are visiting a shady website and you click on a corrupt third-party ad or link. As a matter of fact, no matter how you have been infected, we recommend that you remove Zayka Ransomware from your computer as soon as possible.
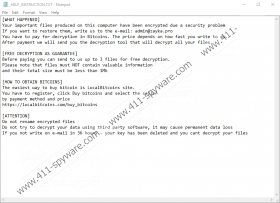
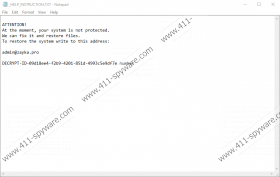
This family is known to use the RSA-2048 encryption algorithm to encode your precious files, which is virtually impossible to crack. In this attack you may lose all your photos, videos, documents, and archives, which are usually targeted by most ransomware programs since it is most likely that you would pay money to get these files back. The encrypted files get a new encoded name that is made up of 32 random-looking letters and numbers plus a “.ZAYKA” extension. This ransomware program creates its ransom note (“_HELP_INSTRUCTION.TXT”) text file on your system. This file contains information about how you can get more instructions regarding the payment for the decryption key.
You have to write an e-mail to “admin@zayka.pro” and you are supposed to get a reply with the details of the Bitcoin address and the amount you have to transfer. It is never safe to make contact with criminals, let alone paying them money. If you do not want to risk losing your money on top of your files, we suggest that you remove Zayka Ransomware without a second thought.
It may take a few minutes for you to eliminate this threat fully but if you follow our guide below, you should be able to do it. First, you need to delete all possible scheduled tasks and then, the related files. If you want to restore and keep security on your PC, we advise you to update all your programs and drivers regularly as well as keep away from suspicious sites and clicking on third-party ads. However, for the best protection possible, we recommend that you employ a reliable anti-malware tool, such as SpyHunter that can automatically avert all known malicious attacks.
How to remove malicious scheduled tasks
- Launch the Task Manager by pressing Ctrl+Shift+Esc simultaneously.
- Select the Start-up tab.
- Identify and select the malicious program and click Disable.
- Exit the Task Manager.
- Open the File Explorer by pressing Win+E.
- Locate the %WINDIR%\Tasks and %WINDIR%\System32\Tasks folders.
- Delete the random-name task.
- Empty the Recycle bin.
- Press Win+Q and type regedit. Hit Enter.
- Delete these random-name value names:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\00FF0EBCF2F2 (value data: “C:\Users\user\AppData\Roaming\BC0EBCF2F2.exe”)
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\BC0EBCF2F2 (value data: “C:\Users\user\AppData\Roaming\BC0EBCF2F2.exe”)
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce\*BC0EBCF2F2 (value data: “C:\Users\user\AppData\Roaming\BC0EBCF2F2.exe”) - Close the editor.
How to remove Zayka Ransomware from Windows
- Tap Win+E.
- Open the “%APPDATA%” folder.
- Delete the random-name malicious file (e.g., “BC0EBCF2F2.exe”).
- Delete all suspicious files that you have saved lately.
- Remove all the ransom note files.
- Empty the Recycle Bin and restart your computer.
Zayka Ransomware Screenshots: