WannaDie ransomware Removal Guide
WannaDie ransomware is a malicious computer infection that targets Russian-speaking users. It looks very much like the notorious WannaCry Ransomware, but it looks like the similarities are there to scare the victims into paying ransomware as soon as possible. While a public decryption key for this infection is not available at the moment, it is possible to remove WannaDie ransomware from your computer without much difficulty. After manual removal, we would still recommend scanning your PC with a reliable security application because you might have a lot more threats on-board and you definitely need to terminate them all.
It is very likely that the infection enters your system through spam email attachments. Spam email campaigns are the most common ransomware distribution tools used by cyber criminals, but that is not the only route out there. Sometimes, programs like WannaDie ransomware can be distributed via web site exploits and even manually through corrupted remote desktop client connections. So it is more than obvious that users need to be extremely careful when they browse the web because danger lies behind every corner. If you encounter suspicious or unfamiliar content, it would be for the best to close the window that has led you to it.
When this infection enters target computer, it first scans for the files it can encrypt. According to the information gathered by our research team, WannaDie ransomware does not encrypt every single file on the affected computer. It mainly goes for the files in the following directories:
- %USERPROFILE%\Recent
- %USERPROFILE%\My Pictures
- %USERPROFILE%\My Music
- %USERPROFILE%\My Videos
- %USERPROFILE%\Favorites
- %USERPROFILE%\Desktop
These are actually the most common default directories for user’s files. If you use the default folders given by the operating system, then it is clear that your files will be encrypted. However, quite a few users create their own directories that do not fall into the same path that is scoured by the ransomware infection. So there might be a chance that some of your files survive if they are saved someplace else.
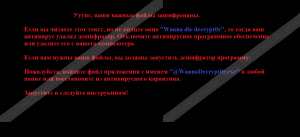
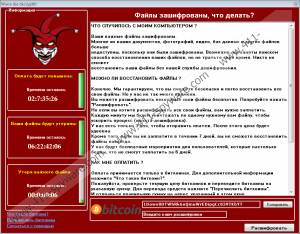
Once the encryption is complete, WannaDie ransomware will change your desktop, disable Task Manager and drop the ransom note that will turn your day sour. The ransom note is entirely in Russian, and if you do not speak the language, it will probably look even more intimidating. The ransom note is rather generic because it says what most of the ransomware notes do: your files have been encrypted, and now you have to pay to get them back.
WannaDie ransomware gives users three days to pay the ransom for the decryption key. Also, it says that if you fail to pay within seven days, you will not be able to restore your files anymore. So the infection threatens you and holds your files hostage, but you should not fall for this scam.
Below you will find manual removal instructions that will help you deal with this intruder. Should you experience difficulties trying to delete WannaDie ransomware from your system, please leave us a comment. Also, do not forget that you should acquire a licensed antispyware tool to protect your PC from other infections in the future. And you should also consider keeping a backup of your files in an external hard drive. Just to be safe.
How to Delete WannaDie ransomware
- Press Win+R and the Run prompt will open.
- Enter %USERPROFILE%\Desktop into the Open box and click OK.
- Delete these files from the directory:
a.wndi
d.wndi
proc.bat
pros.vbs
t.wndi
@WannaDecrypt0r.exe
@WannaDecrypt0r.png - Perform a full system scan.
WannaDie ransomware Screenshots: