SnakeLocker Ransomware Removal Guide
SnakeLocker Ransomware is a recently discovered ransomware-type program that should encrypt your files. However, the good news is that it currently does not do that. It seems that this program is still being developed and was released half-finished, probably for testing purposes in the real world. Therefore, most of the information presented in this article is subject to change. Nevertheless, we think it is important to provide such information about this program as it currently stands. Fortunately, you can also remove it before it can do any damage to your files because ransomware is usually set to encrypt files upon infection.
Our analysis has revealed that SnakeLocker Ransomware was coded in the Python programming language, the same language used for coding Pickles Ransomware. This ransomware should encrypt files with a combination of AES and RSA encryption algorithms, but testing has shown that it does not do that. We believe that this program was released for testing purposes because it was configured to encrypt files in locations where users do not normally place personal files. Our analysis has revealed that it was set to encrypt files in %LOCALAPPDATA%\Google\Chrome\User Data\[USER PROFILE]\Extensions, %LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files, %APPDATA%\Microsoft\Windows\Cookies. Another reason why this program is most likely a test version is that its Tor website whose link is presented in the ransom note is offline. Also, it does not connect to any server, so it does not send a decryption key anywhere. It could also mean that the encryption key is stored locally and is not assigned by a server.
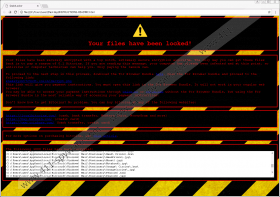
The encrypted files should be appended with a “.snake” or “.TGIF” file extension. The extension depends on the iteration of SnakeLocker Ransomware as there are currently two, but both of them do not encrypt files, and both are semi-functional. Yet the developers want you to pay 0.1 BTC which is an approximate 280 USD. Even though this ransomware does not encrypt any files, it drops a ransom note named INSTRUCTIONS-README.htm on the desktop and opens it automatically. The note contains information on how to get the Tor browser and where to send the ransom to. The good news is that you do not have to comply with any of the demands of the cyber criminals. Now let us discuss this program’s possible distribution methods.
The information we have received suggests that this ransomware may be distributed on malicious websites that feature exploit kits that download this ransomware onto your PC secretly. The exploit used to do that is not known, but an exploit is typically embedded into a website, and the infection is triggered when a user interacts with certain content. However, it is more likely that its developers use email spam as it can offer a more efficient distribution method. However, currently, the infection numbers for this ransomware are low. In any case, the emails should feature the main executable that you either run or download and then run and it starts encrypting. The emails can be disguised as legitimate and pose as receipts, tax return forms, and so on. So we advise caution when opening emails from unknown addresses as you may get an unpleasant surprise.
While SnakeLocker Ransomware is currently incapable of encrypting your files, it may do that in the future, so you should consider yourself lucky if your PC has become infected with this non-working version. You can remove this ransomware manually or get an anti-malware program such as SpyHunter to delete it for you. Locating the executable can be tricky, but the guide below features the most likely locations.
Manual Removal Guide
- Press Win+E keys.
- In the File Explorer’s address box, enter the following file paths and press Enter.
- %USERPROFILE\Downloads
- %USERPROFILE\Desktop
- %TEMP%
- Identify the ransomware’s executable.
- Right-click it and click Delete.
SnakeLocker Ransomware Screenshots: