Shadow Ransomware Removal Guide
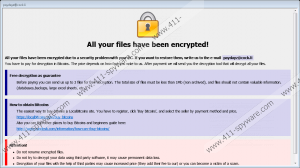
The Shadow ransomware is a destructive infection that encrypts files of different formats and demands a ransom from its victim. Once files are encrypted, the infection displays its warning in a program window and a separate .hta file named "payday", which is created in the %APPDATA% directory. It is important not to panic whenever you face such a system breakdown so that you do not make unnecessary actions. It is also important ignore the requirements provided by the infection and immediate act to remove it from the computer.
The Shadow ransomware is a piece of malware created only for financial gain. The ransom warning of the Shadow ransomware does not provide a precise release fee, because, according to the warning, the ransom depends on how quickly a victim sends an email to paydayz@cock.li. In the warning, a victim is told that the Bitcoin currency must be used to submit a payment. Bitcoin is a digital currency that has gained in popularity among cyber crooks because of the anonymity enabling crooks to remain unidentified and continue working on their ransomware campaigns.
The people behind the Shadow ransomware encourage their victims to take action by offering them a chance to have up to 3 files decrypted. Unfortunately, the total size of the files has to be not bigger than 1 MB, and the files cannot contain any valuable information. This strategy is employed to earn victims' trust, and has been observed in many strains of ransomware in the past. Unfortunately, the chance given by the attackers to have some files recovered does not mean anything. After submitting the release fee you are likely to remain without access to your data. Instead of bothering yourself thinking whether it is worth paying the ransom. You should remove the Shadow ransomware and take measures to prevent such incidents in the future.
The Shadow threat belongs to a ransomware family known as BTCware, which includes threats with very similar characteristics. For example, the Nuclear ransomware is another variant reportedly discovered in late August, 2017. Both the Shadow ransomware and the Nuclear ransomware are very similar visually. On top of that, they behave in a similar manner. For example, the threats add similarly formulated file extensions to encrypted files. The Shadow ransomware appends the extension .[paydayz@cock.li]-id-667.shadow, in which the email address in the square brackets may differ in slightly different variations. The Neclear ransomware also adds an extension that contains an email address in square brackets and a word following the email address.
The Shadow ransomware scans the system and bypasses the C:\Windows directory. Even so, file formats such as .exe, .dll and many others get affected once the infection accesses the computer. All these files should have been copied to a separate device so that you can safely restore them to the computer after removing the infection. Making backups of your files is highly essential so that you do not have to spend money on decryption that is not likely to take place. Additionally, it is important to be aware of potential threats that might cause some privacy-related issues. For example, spam and phishing emails, and weak Remove Desktop passwords are used to spread malware, and, if you are careless with the content you are provided with or pay no attention to your PC's settings, you might not like the consequences. It is also vital to keep the PC protected by a reputable security tool so that you can be sure that you are safe whenever the computer is connected to the Internet.
Removing the Shadow ransomware is extremely important so that the infection does not cause the installation of other threats. An unprotected PC is a sitting target for malware, so you should not wait any longer. Below you will find our brief removal guide that should help you get rid of the malicious threat. After deleting questionable files, you should make sure that the system is free of malware, which you can do using our recommended tool. Bear in mind that computer threats are installed surreptitiously and collect or damage data without your knowledge, so if you do want to be safe online, take the appropriate measures as soon as you can.
How to remove the Shadow ransomware
- Check the desktop for recently downloaded files. Delete all questionable files.
- Access the %APPDATA% directory and delete the file payday.hta.
- Delete questionable files from the Downloads folder.
- Empty the Recycle bin after deleting all suspicious-looking files.
Shadow Ransomware Screenshots: