Retis Ransomware Removal Guide
Retis Ransomware is a new danger to the files stored on your computer if you are French speaker. We have found that this ransomware program mostly attacks French-speaking users and encrypts their personal files. As a matter of fact, this version only limits its encryption to certain main default media directories. In other words, if you are not in a French-speaking country or you do not keep your precious files in the targeted directories, chances are your files are all safe. Still, this is a threat that you should take seriously even if this first version may not be a finished product. It seems that there is no way for you to transfer the ransom fee since it is not possible without an address. In any case, we may have a way for you to decrypt your files. And, then, you can remove Retis Ransomware from your PC.
This ransomware program has been found spreading in spam e-mails as a malicious attachment. This attached file can show up as an image or a text document but it is indeed the malicious executable file. You may wonder why anyone would open such a file or spam. Well, it is not that hard when this spam may appear to be a "must-see" for you. Curiosity is something most people cannot resist. Therefore, when you find a mail in your spam folder that claims to have come from the local police, your bank, your Internet provider, a well-known hotel chain, it is quite likely that you would consider it authentic and even important for you to check out.
And, then, there is the subject line that would push you even more since it may relate to an unsettled invoice, an online booking gone wrong, problems with your credit card details, and so on. Now you see why it is likely that even you might open this mail wanting to see the attached file for more information. However, that would be the greatest mistake since normally there would be no way back from that point and you could not possibly delete Retis Ransomware without losing your files to encryption. It is only by sheer luck that in this particular case you may have a way out, i.e., a way to decrypt your files. But once this malware infection is finished and a new version is released, it is quite likely that there will be no such option.
Similarly to most other ransomware infections, this threat also uses the AES encryption algorithm to render your important files inaccessible and unusable. This vicious program targets your files with ".txt", ".doc", ".docx", ".xls", ".xlsx", ".ppt", ".pptx", ".jpg", ".jpeg", ".png", ".one", and ".pdf" extensions in "%USERPROFILE%\Desktop", "%USERPROFILE%\Documents", and "%USERPROFILE%\My Pictures" directories and subfolders. The affected files get a ".crypted" extension. After the execution, this ransomware opens the Command Line window for a short time with a text, "Hack Lab by Retis," and changes your desktop background.
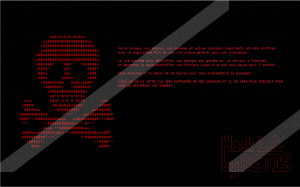
The new background image is indeed the ransom note, which is in French language. It is on black background using red letters. There is a huge skull and bones on the left made from "$" signs and the "U" letter. This note informs you that you have 24 hours to pay the ransom fee or else, you will lose your files. However, there is no Bitcoin address given and no ransom amount mentioned either. Since there is also no e-mail contact provided, there is no way for you to do anything really. This is one of the reasons why we believe that this may not be the finished threat. Yet, we advise you to remove Retis Ransomware immediately because it is still considered a dangerous infection.
We have found that you can actually decrypt your files yourself if you can locate the malicious executable. All you need to do is create a shortcut for the .exe file with an extra argument. In the Properties of the shortcut, you need to add an argument to the Target line after the end quotes:"C:\Users\user\Desktop\Retis Ransomware.exe" /dechiffre. This should work with this current version but there is no guarantee that you will be able to use this trick with the full version. Thus, it may be time for you to start saving regular backups on a removable drive or to cloud storage. Please follow our instructions below if you would like to put an end to this dangerous threat manually. But if you want to protect your PC automatically from future attacks as well, we suggest that you install a reliable malware removal application like SpyHunter.
How to remove Retis Ransomware from Windows
- Press Win+E.
- Locate all recently downloaded suspicious files with the description "RANSOMWARE" and delete them.
- Delete the background image "%APPDATA%\RANSOM.png"
- Empty your Recycle Bin.
- Restart your PC.
Retis Ransomware Screenshots: