Reetner Ransomware Removal Guide
Reetner Ransomware is supposed to be a malicious file-encrypting program, but to our knowledge, the threat does not have such ability yet. Nevertheless, the hackers who created it made the malware show warning messages claiming otherwise. The strangest part is that these warnings do not mention how the user should contact the infection’s developers or purchase decryption tools. If you wish to know more about this rather unusual threat we encourage you to read the whole article. For users who wish to get rid of Reetner Ransomware, we would advise using our recommended deletion steps available below the text. Also, provided you have any questions about the malicious program or want more help with its removal, do not forget you could contact us via social media or leave a message in the comments section.
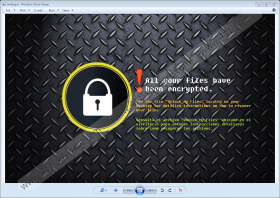
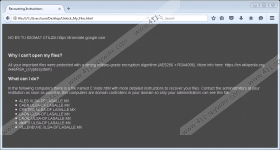
The research reveals Reetner Ransomware should be targeted at users who either speak the English or Spanish language. Our specialists believe it to be true since the infection’s developers created warning messages are written in both of these languages. One of the messages or to be more precise the shorter one could be found on an image titled wallpaper.bmp located in the %TEMP% directory, while the main ransom note with longer text might be scattered in many different folders; its name is Unlock_My_Files.html. As we said earlier in the article, the threat’s messages do not demand to make any payments or contact the hackers.
The file called wallpaper.bmp only says your data was encrypted and advises to open Unlock_My_Files.html. The later file claims the malware locked all important user’s files with extremely secure cryptosystems called AES and RSA. Then it should instruct the user to look for another file created by Reetner Ransomware too. Our researchers who tested the malicious program did not find such a file, which suggests the infection could be not fully developed yet or its developers made some mistakes, although the first variant is probably more likely to be true since the threat does not even lock any data as the ransom note claims.
In conclusion, if you come across Reetner Ransomware, it should not damage any of your files, unless the malware gets updated. Currently, it only replaces background image and drops numerous warning messages in different locations. The recommended deletion steps available below will list these locations and show you how to erase all of the malicious program’s created files manually. If this process looks too complicated for you, we would advise using a trustworthy security tool instead. A legitimate antimalware tool could not only allow the user to eliminate this ransomware but also erase all other possible threats and clean the computer. Not to mention it could guard the system from malware you could yet come across if you keep it up to date.
Get rid of Reetner Ransomware
- Press Windows key+R.
- Insert Regedit and press Enter.
- Find this path: HKCU\Control Panel\Desktop
- Right-click a value name called Wallpaper and press Delete.
- Exit Registry Editor.
- Press Windows key+E.
- Navigate to: C:\Users\User\AppData\Local\Temp
- Right-click an image called wallpaper.bmp and choose Delete.
- Go to your %USERPROFILE%\Desktop, %USERPROFILE%\Downloads, and %TEMP% directories.
- Find a malicious file that was opened before the system got infected.
- Right-click it and press Delete.
- Locate and remove all files titled as Unlock_My_Files.html from the %ALLUSERSPROFILE%, %APPDATA%, %LOCALAPPDATA%, %PUBLIC% directories and their subfolders.
- Leave the File Explorer and empty your Recycle Bin.
- Reboot the PC.
Reetner Ransomware Screenshots: