Purge Ransomware Removal Guide
If you cannot open your files and they have a second extension called “.purge,” you may have infected the system with Purge Ransomware. As you see, the threat was named after the extension that it adds to the affected data. The malware should apply this extension to every file that it encrypts with the RSA algorithm. The bad news is that the malicious application is programmed to lock text documents, images, photographs, videos, and other personal files. However, if you have any copies of such data on removable media devices or somewhere else, you can easily recover it. In any case, we advise you to erase the threat from the computer. Purge Ransomware could be removed with a trustworthy antimalware tool or by following the manual deletion instructions available below. For more information about the infection, continue reading the article.
It is most likely that you installed the malware without even realizing it. Apparently, Purge Ransomware could travel with malicious files that might be spread through infected email attachments. The worst part is that such data could be disguised as harmless text files, invoices or other documents. Therefore, some users might launch it without even thinking that it could be malicious. In such situations, users should always take extra precautions, especially if data they received comes from an unfamiliar source.
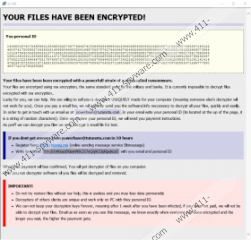
As soon as you launch the malicious file, Purge Ransomware should place its data on to the system. Then, the infection should begin encrypting personal data on user’s computer. It enciphers various personal files and adds the “.purge” extension to them. Also, the malware should create a unique decryption key and personal user ID. According to the ransom note which is displayed right after the encryption process is over, both the unique ID number and decryption key are needed to recover locked data. Unfortunately, the user gets only his unique ID number, while the decryption key is known to the malware’s creator.
The ransom note urges users to contact the infection’s developers through email. It says that the reply answer will explain to users how much they need to pay for the decryption tools and how to make the payment. You might think that this is an easy way to unlock your valuable data. Based on other similar malware infections it is possible that the ransomware’s creators could ask you to pay a few hundred or even more than a thousand US dollars. Given that there are no guarantees they will send the decryption key, transferring the money could be extremely risky. In the end, you might end up losing not only data on the computer, but some of your savings as well.
Naturally, we advise you to eliminate Purge Ransomware instead of paying money to its developers. To get rid of the infection, users would need to locate and erase the main executable file and ransom note. If you need a guide, you should slide a little below and have a look at the removal instructions. We could also recommend you a trustworthy antimalware tool that should locate the malware automatically and help you delete it too. This way you would also get rid of other possible threats and obtain a reliable tool that could help you keep the system secure.
Eliminate Purge Ransomware
- Press Win+E to open the Explorer.
- Copy and paste this path: C:\Users\user\AppData\Local into the Explorer and press Enter.
- Search for a file titled as msiscan.exe.
- Mark the file, right-click it and press Delete.
- Check your Desktop; there should be a file called “How to restore files.hta.”
- Right-click this file and click Delete.
- Empty the Recycle bin.
Purge Ransomware Screenshots: