Parisher Ransomware Removal Guide
Parisher Ransomware can slither onto your system without your knowledge if you use remote desktop connections and software. This ransomware is a major hit to your computer as it uses a strong unknown algorithm that cannot be hacked as of yet. Strangely enough, this dangerous infection “only” targets your document files. It is quite likely that you lose them for good unless you can pay these criminals the insanely high ransom fee. In fact, it is possible that this ransomware program is aiming at companies, which could be a good reason for such a price to pay and also an explanation about the documents in its crosshairs. In any case, if you find this ransomware on your computer, you had better pray you have a recent backup saved on an external hard disk of some sort because otherwise you may not see your files again. We do not recommend that you pay the ransom fee because, as always in such cases, there is no guarantee that you will get the decryption key or tool. We advise you to remove Parisher Ransomware immediately after you notice its presence. Let us tell you how this vicious program can appear on your computer and what you can do to avoid similar attacks.
We have discovered that this ransomware program is actually a new variant of Mobef Ransomware. This infection does not use the good old method of spamming campaigns to spread its poison but, instead, it attacks through Windows RDP (Remote Desktop Protocol) and Microsoft RDC (Remote Desktop Connection) software as well as, in some cases, TeamViewer or other remote desktop systems. It is possible that these crooks get hold of your credentials or exploit open sessions somehow. Once they gain access to your system, they drop this malicious threat, which initiates the attack right away.
Although we have not yet found proof, it is possible that in the near future this infection evolves and it will start spreading via other channels, such as spam e-mails and Exploit Kits. Therefore, we are here to tell you what you can do to avoid these. Spam e-mails have become rather tricky and convincing and it is possible that not only can they evade your spam filter but they may also be able to make you believe that it is a must for you to open them and check out the attached file. Obviously, this attachment is not what it is said to be and seems to be. It is indeed a malicious executable file posing as an image or document claimed to be an unpaid invoice or proof for wrongly given credit card details. Most users fall for such tricks and rush to download and open the attached file. This is when they actually activate the attack. And, this is why you need to be more cautious around your e-mail folders.
Another precaution for you to consider is to keep your browsers and drivers always updated. Criminals can use so-called Exploit Kits to set up a trap, i.e., a malicious website. It is enough for you to load this page and the malicious code disguised as a banner or any other Flash or Javascript content could drop this ransomware or any other infections onto your computer. The biggest problem with ransomware attacks is that even if you delete Parisher Ransomware after you realize you have been hit, it is too late to save your files from encryption.
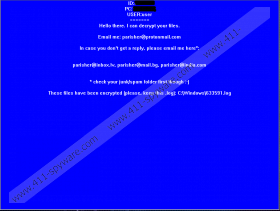
As we have mentioned, this ransomware targets your document files, such as ".pdf," ".txt," ".xml," ".docx," and so on. It uses an unknown but strong algorithm to encrypt your files. The affected files do not get any extra or new extension. Three files are dropped onto your system: "HELLO.0MG," which is the ransom note in text format, it is created in every %USERPROFILE% subfolder, "LOKMANN.KEY993," which is a 1024-bit key and could be used for encryption or decryption of a key, it is created in every %USERPROFILE% subfolder, and finally, "[6 digit ID].log,” which is the list of the encrypted files placed in the %WINDIR% directory. When all the operations are finished, a blue screen comes up on your desktop whose color resembles BSOD screens. This is the ransom note window and it remains always on top so you cannot move it out of the way.
You learn from this note that the criminal or criminals claim that they can decrypt your files. There are no details shared at this point, only a primary e-mail address to contact (“parisher@protonmail.com”) and three secondary ones, including "parisher@inbox.lv." User reports indicate that these criminals may demand a shockingly high, 5 Bitcoins ransom fee, which is around 3200 US dollars. We have mostly seen such demands when criminals attacked hospitals or companies since it would be doubtful that any simple personal user could pay this amount for some old text files or even new ones for that matter. It is up to you, though, whether you risk losing this money too on top of all your documents. If you want to be safe on your computer again, we suggest that you remove Parisher Ransomware ASAP.
It is not too complicated to eliminate this dangerous threat. We have included instructions which you need to follow step by step to make sure that no leftovers remain. If you do not want to risk manual removal, though, we suggest that you find a decent anti-malware program, such as SpyHunter, and let it automatically clean your system of all possible threats. If you keep this software always activated and up-to-date, you could have peace of mind finally and you would not have to be afraid to land on suspicious sites ever again. If you have any questions about how to remove Parisher Ransomware, please leave us a comment below.
How to remove Parisher Ransomware from Windows
- Before you close the ransomware program, open up the Task Manager by pressing Ctrl+Shift+Esc.
- Find the malicious process.
- Right-click on it and choose Properties.
- On the General tab, check the Location field to find out where it is running from. (It could be in these directories: %APPDATA%, %TEMP%, and %LOCALAPPDATA%)
- Go back to the process list, click on the malicious process, and press End task.
- Delete "HELLO.0MG" and "LOKMANN.KEY993" from every %USERPROFILE% subfolders.
- Bin the log file from %WINDIR% (Its name will be the 6-digit ID you see in the ransom note.)
- Empty your Recycle Bin.
- Restart your computer.
Parisher Ransomware Screenshots: