Mobef Ransomware Removal Guide
So here we are again with another Trojan called Mobef Ransomware. It has been classified as ransomware because it is set to encrypt your personal files once it enters your computer. Therefore, you must prevent this infection from entering your PC and remove it as soon as possible if it manages to creep in. Since it is a relatively new infection, not much in known about it but we will provide you with as much information currently available about it. Unfortunately, at this point, there is no method of decrypting the files that this ransomware encrypts using third-party software, but we do not recommend that you pay the ransom in the hope of getting the working decryption key from the developer. From the outset, we want to say that it is a low-grade malware developed by amateurs, so the chances are that you will not receive the decrypter once you have paid.
This infection was first seen in mid-April and since then it probably has infected many computers. Still, Mobef Ransomware’s distribution methods remain elusive. There is no information about how it enters a computer because users do not notice the infection until it “goes to work.” So we will just go over the most common ransomware distribution methods to give you a better idea of how your computer could have gotten infected with this ransomware.
The most effective method used to disseminate ransomware is, without a doubt, email spam. Cybercriminals obtain lists of email addresses from shady sources, often they get them from online advertising companies, and configure their server to send email spam. Ransomware is usually included in an attachment, usually a self-extracting archive that drops the files once you try to open the archive. Furthermore, ransomware is often distributed using compromised websites that host a download of the infection disguised as an entirely different program. Also, such infections are often promoted via adware-type software that disguises its installer as a Java or Flash Player update. However, we are barely scratching the surface here, but now you have a better idea of how your PC can or could have gotten infected with Mobef Ransomware.
Mobef Ransomware is a tricky infection to detect manually because there are several versions of it, and its process name is the same as its executable name. In other words, it can disguise itself as another program and run unnoticed. In some cases, this ransomware is known to masquerade as Java(TM) Platform SE binary. If you do not have an anti-malware program, then try opening the Task Manager and going through the list of running processes and opening their locations. We have found that this ransomware modifies a system file at C:\Users\user\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content and C:\Users\user\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData. This file is named (07CEF2F654E3ED6050FFC9B6EB844250_5F5269AC0D922158A5B542020448A2D3.) However, some versions of this ransomware might contain a Ransom.Mobef.A.exe file located at %APPDATA% or %TEMP%. Now that you know how to find its location let us take a look at how this program works.
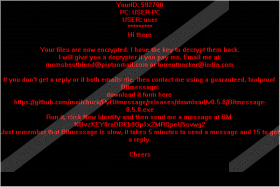
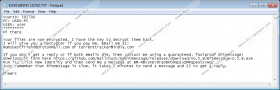
Once on your computer Mobef Ransomware connects to its primary server at 192.185.16.132 (kentamplin.net domain.) Then it begins to scan your computer for files to encrypt. Once it has completed the scan, it will encrypt files types, such as .3ds, .4db, .4DD, .7z, .7zip, .doc, .docm, .docx, .dot, .rar, .raw, rpt, .rtf, .saj, and so on. In other words, it will encrypt all files that are not vital to running the operating system. While encrypting, it will drop two files in every folder in which it has encrypted a file. Depending on the version of the ransomware it will drop either 419Date00ABC.KEYHOLES and 420DateINFECCIONZ.TXT or 4152016000.KEY and 4-15-2016-INFECTION.TXT (the file name contains the date of the infection.) The .TXT file contains a ransom note which states “Your files are now encrypted. I have the key to decrypt them back” and gives you instructions on how to contact the cybercriminals to get the necessary decryption key. We found that this ransomware uses DES, RSA and AES algorithms to encrypt the files, but this ransomware’s developers were sloppy, and the result is a semi-functioning encryption. This ransomware does not add a file extension to the encrypted files but still renders them inaccessible. Malware researchers might develop a decryption tool, but until then all you can do is delete this ransomware and try to recover your files.
We hope that the information we have provided in this article was useful. Our research has revealed that Mobef Ransomware is a low-grade yet dangerous Trojan that can damage your personal files beyond repair. We urge you not to pay the ransom because you might never receive the decryption key. Therefore, you should remove Mobef Ransomware and try to restore your files using file restoring software or Shadow Volume Copy Service.
Mobef Ransomware Screenshots: