Karmen Ransomware Removal Guide
Karmen Ransomware is a new Hidden Tear infection that was created using the same source code as other well-known infections, including Gc47 Ransomware and Redants Ransomware. It is most likely that these infections were created by different parties, and so the distribution can be unique in every case. Some malware creators choose to spread their products via malicious download websites. Others hide the malicious launchers within inconspicuous-looking spam emails. In some cases, users are tricked into launching the ransomware infections themselves, and, in other cases, they could be downloaded by other active threats without their permission. Unfortunately, ransomware is stealthy, and it can slither into your operating system without any warning. Once you learn that this malware is active on your PC, it might be too late to do anything to stop it. Although deleting Karmen Ransomware is the most important thing, we suggest reading this report before you jump to the removal guide below. If you do not find answers to the questions you have in this report, use the comments section below to start a conversation.
The main target of Karmen Ransomware is personal files. If this infection successfully encrypts your photos, important documents, and other valuable files, it might have a chance at making you pay a ransom. According to our researchers, a file called “decrypt.exe” (you should find it in the %TEMP% directory) is the one responsible for the encryption process, and it should be created by the threat upon execution. When the ransomware encrypts your files, it attaches the “.grt” extension to their original names. Nothing will change if you rename the file and remove the extension, so do not waste your time with that. It is not yet known which encryption method this malware employs, but it is unlikely that legitimate file decryptors could help you out. To recover your files you need a special decryption key, and we cannot even confirm that it exists. Of course, it is most likely that the cyber criminals behind Karmen Ransomware store this key on a remote server, but we do not know if they would provide it to you even if you paid the ransom that is requested via a special window that pops up soon after the encryption is complete.
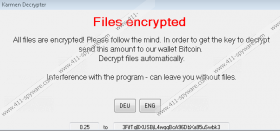
The message within the Karmen Ransomware ransom note is represented in two languages: German and English. Needless to say, this threat is likely to be spread in countries where these languages are spoken, but, considering that English is known all across the world, it is difficult to say how wide this threat could cast its net. The ransom note informs that you need a decryption key and that you can retrieve it by paying a ransom to a specified Bitcoin Address. The amount of the ransom and the Bitcoin Address are shown at the bottom of the message. Here is the question: Are you sure that cyber criminals can identify you to provide you with a specific decryption key? Also, are you sure that they will give you the key once you pay the ransom? Unfortunately, the creators of ransomware are not known for their conscientiousness, and so it is highly risky to pay the ransom; especially since it is big. The ransom our researchers were demanded to pay was 0.25 Bitcoins, which, at the moment, converts to $270 or €250.
What should you do if your files were encrypted? You can look into legitimate file decryptors, but it is not likely that they will assist you. You should also think if the encrypted files have backup copies on external drives or online storage. If you end up losing your files, do not forget to set up a backup to protect the remaining and new files in the future. Of course, do that after you remove Karmen Ransomware from your operating system, and you can do that either manually or using automatic malware removal software. We suggest employing software that could delete existing threats and reinforce system’s protection to guard you against all others. If you do not want to invest in anti-malware software, you are left with the automatic removal option, and you can follow the guide below to get rid of the threat.
How to delete Karmen Ransomware
- First tap Ctrl+Shift+Esc to launch Task Manager.
- Terminate the malicious file to disable the ransom note window. Exit Task Manager.
- Find the malicious launcher (e.g., the spam email attachment) and right-click it.
- Choose Delete and then get rid of any other recently downloaded suspicious files.
- Launch Explorer by tapping Win+E keys and enter %TEMP% into the bar at the top.
- Right-click and Delete a malicious file called decrypt.exe.
- Tap Win+R to launch RUN and then enter regedit.exe into the dialog box.
- Move to HKCU\Software\Microsoft\Windows\CurrentVersion\Run (depending on the Windows version, you might have to move to HKCU\Software\Wow6432Node\Microsoft\Windows\CurrentVersion\Run).
- Right-click and Delete the value named DecryptFiles.
Karmen Ransomware Screenshots: