JobCrypter Ransomware Removal Guide
JobCrypter Ransomware is a Trojan-type malware that can encrypt your personal files and demand that you pay a ransom to get the decryption key. Therefore, removing it is of utmost importance. This particular ransomware is somewhat unique because you can retrieve the decryption key while it is still encrypting your files. In our opinion, it is a poorly-made ransomware which is an advantage because if you are quick to react, then you can prevent your personal files getting ruined by an unbreakable cipher. So in this article, we are going to provide you information about how JobCrypter Ransomware is distributed, how it works, how you can obtain the decryption key without paying the ransom, and how to remove it.
We tried to get as much information about this infection as we possibly could, and our labor was not in vain. Let us begin with this infection's distribution methods. We have found that JobCrypter Ransomware is currently being distributed using email spam. The current sender’s email address is Bordeaux@sothis.fr. Note that the emails are sent automatically from a dedicated server. They target random users, but the email addresses of the victims are obtained by means that are not known to us. At any rate, the sent email contains a self-extracting archive that drops its contents into a hidden folder from which this ransomware is run.
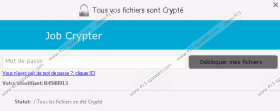
In most cases, the self-extracting archive should drop one executable file named Locker.exe to the %APPDATA% directory. This executable is run automatically, and it scans for specific file types because the cyber criminals are only interested in encrypting personal files — not all files that may render the PC inoperable. For example, this ransomware will search for and encrypt files, such as .bin, .bk, .bmp, .cfg, .dat, .db, .doc, .docx, .gif, .gz, .htm, and .html. The .locked file extension will be added to all encrypted files. Once the encryption process is complete, this ransomware will generate a window for entering the decryption key. Note that everything in JobCrypter Ransomware is written in French, so there is no doubt that this infection is more prominent in French-speaking countries.
In any case, as we mentioned in the introduction, you have the opportunity to exploit this ransomware’s vulnerability and get the decryption key free of charge. Once Locker.exe is launched, it will take approximately 10-20 minutes for it to complete the encryption process. Note that it will only start encrypting if the computer is connected to the Internet, but disconnecting the Internet connection will not stop the encryption. However, you have this small 10-20 minute window to get the decryption key for free. JobCrypter Ransomware temporarily places this key in the Windows Registry. To be more specific, you can find it in HKCU\Software. Its value name is “Code” and it contains a 20 character key. If you manage to obtain the decryption key, enter it in this ransomware’s window.
If you miss this window of opportunity, then you will not be able to decrypt the files using third-party software. JobCrypter Ransomware uses the TripleDES (3DES) encryption algorithm which is tough to crack. You can try using third-party software to decrypt your files, but the chances of success are rather slim. However, we recommend that you not pay the 100 Euro ransom fee, because there is no guarantee that you will get the promised decryption key. Often, malware developers fail to honor their commitments, so you might be just throwing your money away.
To sum up, JobCrypter Ransomware is a Trojan-type infection that uses the TripleDES cipher to encrypt your files and demand that you pay a ransom for the decryption key that you might not get after making the payment. The TripleDES cipher is next to impossible to crack using third-party software. If you have missed the window of opportunity to obtain the decryption key from the Windows Registry, then the only thing you can do is to remove JobCrypter Ransomware. Please use our manual removal guide or our recommended program SpyHunter to wipe out this infection.
Boot up the PC in Safe Mode with Networking
Windows 10
- Open the Start menu and click the Power button.
- Hold down the Shift key and click Restart.
- Select Troubleshoot.
- Go to Advanced options and select Startup Settings.
- Select Restart.
- Select Enable Safe Mode with Networking.
Windows 8/8.1
- Simultaneously press Windows Key+C and click Settings.
- Click Power, hold down Shift on your keyboard and click Restart.
- Select Troubleshoot and go to Advanced options, and then select Startup Settings.
- Click Restart and press 5 on your keyboard to Enable Safe Mode with Networking.
Windows 7 and Vista
- Restart the computer.
- Press and hold the F8 key as your computer restarts.
- On the Advanced Boot Options screen, use the arrow keys to highlight the Safe Mode with Networking, and then press Enter.
- Log on to your computer with a user account that has administrator rights.
Windows XP
- Click the Start button and then click Restart.
- Press and hold the F8 key as your computer restarts.
- On the Advanced Boot Options screen, use the arrow keys to highlight the Safe Mode with Networking, and then press Enter.
- Log on to your computer.
Removal method 1. Delete the files manually
- Simultaneously press Windows Key+E.
- Enter %APPDATA% in the window’s address bar.
- Find Locker.exeand right-click on it.
- Click Delete.
- Empty the Recycling bin.
Delete the registry keys
- Simultaneously press Windows Key+R.
- Enter regedit in the dialog window and click OK.
- Locate and Delete the following registry keys.
- HKCR\Applications\Locker.exe
- HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.locked
- Locate HKCU\Software\Microsoft\Windows\CurrentVersion\Run
- Delete ValueData C:\Users\user\AppData\Roaming\Locker.exe
Removal method 2. Use antimalware
- Open your browser.
- Go to http://www.411-spyware.com/spyhunter
- Click the download button to get our recommended antimalware.
- Run the Installation Wizard.
- Launch the program.
- Select and Run a full system scan.
- Click Fix Threats.
JobCrypter Ransomware Screenshots: