Jack.Pot Ransomware Removal Guide
Before cyber criminals release their programs into the wild, they are bound to make a few test runs, and we believe that Jack.Pot Ransomware is all about that. This infection is still in the development mode, so it is not clear what the program will be capable of when the creators are done tweaking it, but we can still describe some of its features. After all, the man point is that you need to remove Jack.Pot Ransomware from your computer if you happen to have this infection on-board. Tolerating the ransomware and succumbing to its demands will do you no good.
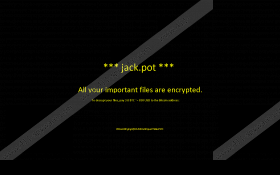
There are multiple symptoms associated with this infection. For instance, when this program enters your computer, it blocks .exe files from running by encrypting them. It also changes your background by locking your screen with a full-screen window that displays the ransom message. It will also connect to the Internet without permission, and you will not be able to remove it via Control Panel. That is rather common among ransomware programs, and they employ such practices to push the panicked users into spending their money. However, that is definitely something you should never do because this is exactly why Jack.Pot Ransomware infects you: it needs your money.
According to our research, the main malicious file for this program was first created on March 14th, 2016. Only a limited number of computers will be infected with this program because it is still being developed. Consequently, it may be hard to say what to expect of this application because the developers may add more functions as they test the program. However, right now we know that Jack.Pot Ransomware uses an unfamiliar algorithm to affect target files, and the infection encrypts files that are located in the %USERPROFILE% directory. It means that most of your frequently-used files could be affected by this program.
Some ransomware applications delete themselves once they drop the main payload. Jack.Pot Ransomware, on the other hand, does nothing of the sort. It does not delete itself after the encryption, and it does not close the process. It means that if you were to transfer new and healthy files into the affected directory, these new files would be encrypted by the ransomware program again. Therefore, before you do that, you need to remove Jack.Pot Ransomware from your computer ASAP.
Does paying the ransom work? Hardly. The BTC address this program uses is false, and so you would not be able to transfer the money. Although we seriously doubt you would want to spend over $800USD for the decryption key that probably does not even exist. Either way, the given address on the screen cannot be identified, so sending the money is pointless. Nevertheless, we have found that the ransomware does communicate with a remote IP address at 54.58.55.93. The address is located in the United States, and it is probably the command and control server for this infection.
Since this is not the complete version of the program, it is hard to say whether the files are or will be decryptable. If you happen to be infected with Jack.Pot Ransomware, you should delete the infection right now, along with your damaged files. You will be able to restore your files if you have a backup somewhere. Also, please do not forget that you should also run a full system scan with a licensed antispyware tool.
How to Remove Jack.Pot Ransomware
- Press Alt+Tab and close the ransomware window.
- Press Ctrl+Shift+Esc to open Task Manager.
- Click the Processes tab and click the malware process in the list.
- Press End process and exit Task Manager.
- Go to your Downloads folder and delete the malicious infection file.
- Run a full system scan with a security program of your choice.
Jack.Pot Ransomware Screenshots: