Guster Ransomware Removal Guide
Guster Ransomware is a new player in the market of ransomware infections. Our research team says that this program is particularly dangerous and annoying. In this description, we will tell you more about the infection, and you will also find the manual removal instructions, which you can use to delete Guster Ransomware from your computer. Please note that removing the infection does not automatically mean that your infected files will be reverted to their original state. You may have to restore your encrypted files from a backup because no public decryption tool is available at the moment.
Our security team says that this program is extremely dangerous as it spreads via email attachments. You may receive an email message that looks like an official notification from some company, but in reality, that attached file will carry the malicious infection that will freeze your system. Hence, you should be really careful about the attachments you open on a regular basis. It is always a good idea to scan unfamiliar files with a security program. If a file is malicious, your security tool will detect that immediately.
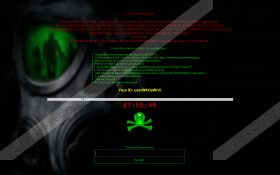
Yet, if you have been infected with Guster Ransomware, you now have to fight it. The program will lock your screen with threatening images that will say the following:
!!! PAY ATTENTION!!!
All of your files (documents, videos, photos, musics, pdfs, etc) have been encrypted with a strong military cryptography. The only way to get your files back to you, is paying a fee of 0.4 bitcoins, which worth something about 300.00 USD.
<…>You have 48 hours to pay me these bitcoins or you’ll never get to see your files again! You’re warned!
If you have never encountered a ransomware program before, this kind of message might seem extremely intimidating, but you should not panic. It is better to find out more about your enemy than just do everything it says.
Guster Ransomware will encrypt your files using the AES-256 encryption algorithm. The program is based on the HiddenTear open source ransomware, which is quite often used by cyber criminals to create their own custom versions of malicious infections. It will target the %USERPROFILE% directory and all of its subfolders. Therefore, if you have some of your files located in other directories, it would be possible to avoid the encryption. It just shows how important it is to keep copies of your files, either in a different directory or on an external drive. After all, when there is no public decryption tool available, the best way to get your files back is to restore them from a backup.
Luckily, the program does not create a Point of Execution, so it means that if you restart your computer, the ransom note will not appear again. Essentially, it is not hard to remove Guster Ransomware from your computer, and this is exactly the thing you should do right now.
If you think that this is too much of a challenge for you, you can rely on a legitimate security application that will remove the infection for you automatically. For more information, do not hesitate to leave us a comment.
How to Remove Guster Ransomware
- Restart your computer and wait for the system to load.
- Open your Downloads folder.
- Find the most recently downloaded files.
- Delete those files and scan your PC with SpyHunter.
Guster Ransomware Screenshots: