Gedantar Ransomware Removal Guide
Gedantar Ransomware is a new dangerous ransomware infection that may have a couple of versions out there already spreading. We have found that certain samples may not even encrypt files on your system or do not use an executable, while others do. In other words, you do need to take this threat seriously because chances are your important personal files have been encrypted with a strong algorithm, probably impossible to crack. These attackers offer you a deal to give you the decryption key if you pay a certain amount; however, in such cases it is very rare that these cyber criminals actually send you anything other than another threat. This ransomware is possibly targeted at Russian speakers due to the fact that the ransom note is in Russian. We believe that the only way for you to restore security on your system is to remove Gedantar Ransomware immediately and use a backup you may store on a removable drive or in cloud to recover your files.
It is quite possible that you opened a spam e-mail and executed its attachment, and this is why you have this dangerous ransomware infection on your system now. This spam can be rather convincing though, it is not the type that you could identify right away. It needs to appear to be authentic so that more potential victims can be turned into actual victims. What these cyber criminals mostly count on is your curiosity. Therefore, such a spam will either contain a "must-see" video or picture, or it will claim to contain important information about an online booking gone wrong, a problem with your credit card information, and so on. This spam can be so convincing that even if you do not feel related to the subject claimed, you would be still likely to want to open it just for the sake of curiosity. But the message usually does not really contain any useful information apart from pushing you to open the attached file for further details. And, this is the point where you can still say no. However, victims go along with it and click to view this attachment. Remember that it is not possible to delete Gedantar Ransomware after this point since by the time you notice its presence, it will have finished encryption on your system.
You can also infect your system with such a dangerous program if you use unfamiliar torrent or freeware sites for downloading free software. These sites are known to promote malicious software bundles, which may carry several malicious threats as well as potentially unwanted programs. We advise you to stick with reputable and official sites to download anything really, including software updates. Finally, you can also harm your system and files big time if you do not update your browsers and drivers frequently. Cyber villains create malicious webpages loaded with Exploit Kits to drop such vicious programs onto your system without your knowledge. If you want to avoid the need to delete Gedantar Ransomware or other infections, you should update all your programs regularly and refrain from clicking on random third-party ads while visiting suspicious websites.
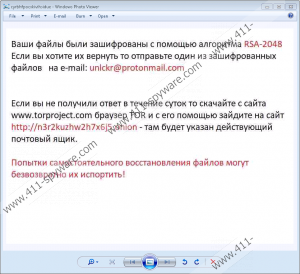
This ransomware may operate through a malicious executable called "Gedantar.exe" but it is also possible that certain versions may just use commands to encrypt files on your system. We believe that this malware infection may still be under development actually. It targets Russian speakers assuming from the ransom note. The working version uses the RSA-2048 algorithm to encrypt your important files. It seems that this ransomware does not append a new extension to the affected files; however, it may insert 8 random characters after the original name like in "myimage_fhrddetz.jpg." The ransom note is a .jpg file with twenty random characters in the file name as in "cyrbhfpocxkivihsidue.jpg." You may find this file on your desktop and possibly in all folders affected by this threat. This note is in Russian and tells you to send an email to "unlckr@protonmail.com" including one small file to be decrypted for free. Then, you need to visit a TOR website to get further instructions about the payment. Although we do not have information yet regarding the amount of the ransom fee, we do not advise you at all to either contact these criminals or to pay them any amount. It is safer to remove Gedantar Ransomware right away.
Hopefully, you are a security-minded computer user and you have a backup saved somewhere so that you can recover at least some of your important files. Please follow our instructions below if you would like to take care of this malicious threat manually. If you do not trust your IT skills, you can always download and install a trustworthy malware removal application, such as SpyHunter. Such security software can automatically defend your PC against all possible potential and dangerous threats as well.
How to remove Gedantar Ransomware from Windows
- Press Ctrl+Shift+Esc to open Task Manager.
- Identify the malicious process.
- Right-click on the process and choose Properties.
- Memorize the Location path of the executable and then, click OK.
- Press End task to kill the process.
- Exit Task Manager.
- Press Win+E.
- Locate the malicious .exe and delete it.
- Check all your default download folders (%Temp%, Downloads, and Desktop) for recently saved suspicious files and delete them.
- Delete all ransom notes.
- Empty your Recycle Bin and restart your computer.
Gedantar Ransomware Screenshots:
Gedantar Ransomware technical info for manual removal:
Files Modified/Created on the system:
| # | File Name | File Size (Bytes) | File Hash |
|---|---|---|---|
| 1 | 33959615d309258d6f0a38c607362143821cc7a96690cd2c6696c112dc5ac64b.exe | 52224 bytes | MD5: 8afcb6e9b45c234bbb5982f382396049 |
Memory Processes Created:
| # | Process Name | Process Filename | Main module size |
|---|---|---|---|
| 1 | 33959615d309258d6f0a38c607362143821cc7a96690cd2c6696c112dc5ac64b.exe | 33959615d309258d6f0a38c607362143821cc7a96690cd2c6696c112dc5ac64b.exe | 52224 bytes |

