DCRTR Ransomware Removal Guide
If you have recently found a notepad file in which you are asked to contact someone at decryptor@cock.li, that means that you are dealing with the DCRTR ransomware, which encrypts files in an attempt to scare you into paying for file decryption. The DCRTR ransomware should be removed from the computer even though its authors suggest decrypting up to 5 files free of charge, which is offered to earn your trust. The odds are that no changes on your computer will be made after you pay the so-called ransom fee, so, instead of spending a considerable sum for not regaining your data, remove the DCRTR threat once you finds it ransom notes.
Upon installation, the ransomware creates its copy msshost.exe in the %APPDATA% directory and also creates its two points of execution in different hives of the Windows Registry. One of the points of executions is created in the HKEY_LOCAL_MACHINE hive, in which information about installed software is contained, whereas the other point of execution is created in HKEY_CURRENT_USER, in which software information related to the currently logged user is stored.
The DCRTR ransomware is also programmed to stop six processes if any of them is running. The processes include WSCSvc, WinDefend, wuauserv, BITS, ERSvc, and WerSvc. For example, wscsvc stands Windows Security Center Service which enables access to different security settings, such as Windows Firewall and others.
After killing system security-related processes, the infection deletes Windows shadow copies using several commands and kills these processes: MSExchange*, Microsoft.Exchange.*, sqlserver.exe, sqlwriter.exe. For example, the sqlwriter.exe file must be running alongside the Volume Shadow Copy Service application to ensure a successful backup or restore process.
The DCRTR threat employs AES and RSA encryption methods to encode different files. After encrypting a file, the infection adds the extension .[decryptor@cock.li].dcrtr, hence the name of the threat. Additionally, every affected file gets a token named {LAMA}, which is possibly used for file identification.
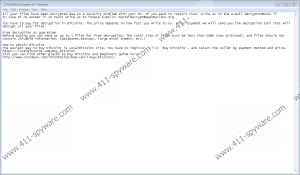
After completing the encryption procedure in each folder, the infection creates a ransom note file so that the victim easily finds an explanation for the unexpected changes on the computer. In the ransom file ReadMe_Decryptor.txt, the victim is instructed to contact the attackers by email at decryptor@cock.li. If no reply is received in 24 hours, the alternative email address masterdecrypt@openmailbox.org is supposed to be used. The emails are given so that the victim can found out the amount of money that has to be paid for decryption. The ransom warning only specifies that the release fee is to be pain in the Bitcoin currency, which has gained its popularity among cyber crooks over the few past years.
Usually, a ransom warning would contain a specific sum requested by the attackers, but there are some cases, as with the DCRTR ransomware, when the release fee depends on how quickly the victim reaches out to the attackers. However, the sum should not matter because there is no need to pay up. The possibility of regaining access to the affected files is extremely low, so the removal of the infection should follow the detection of this threat.
Do not delay the removal of the DCRTR ransomware, because your computer is likely to be vulnerable to many other threats circulating on the Internet. An unprotected operating system can be easily infected by adware, browser hijackers, data stealing trojan, and, without a doubt, other ransomware threats that are capable of disabling various built-in security settings.
Our advice is that your implement a powerful anti-malware tool to have the DCRTR ransomware removed and the system protected. It is also possible to delete DCRTR manually, which you can do with the help of the removal guide given below, but bear in mind that by choosing this option you do not solve the security issue. If you continue browsing insecure websites, clicking on pop-up ads, and checking all unrecognized or questionable emails, you put yourself at risk of getting your data compromised. Do not hesitate to shield the system from malware and ransomware attacks, because this is how you can have safe web browsing sessions.
How to remove the DCRTR ransomware
- Check the desktop and Downloads directory for the malicious file and delete it.
- Access the %APPDATA% directory and delete the malicious file msshost.exe.
- Follow these pathways and delete the malicious registry values:
HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run::MssHostEngine
HKCU\Software\Microsoft\Windows\CurrentVersion\Run::MssHostEngine
DCRTR Ransomware Screenshots:
DCRTR Ransomware technical info for manual removal:
Files Modified/Created on the system:
| # | File Name | File Size (Bytes) | File Hash |
|---|---|---|---|
| 1 | ReadMe_Decryptor.txt | 1033 bytes | MD5: f6e2620366a131df0d34a08297a34134 |
| 2 | DCRTR Ransom.exe | 254464 bytes | MD5: 08945d816ef948fa28ecbf0791ccb061 |
Memory Processes Created:
| # | Process Name | Process Filename | Main module size |
|---|---|---|---|
| 1 | DCRTR Ransom.exe | DCRTR Ransom.exe | 254464 bytes |

