CryptoRoger Ransomware Removal Guide
CryptoRoger Ransomware does not simply ruin your day when it enters your computer silently, but it also ruins your most important files on your hard disk. This ransomware is a real nightmare since it can encrypt all your images, videos, audios, and documents practically within a few minutes. It is impossible to decrypt your files without the private key that is kept hidden on a remote server, which can only be accessed by the criminals who created this vicious program. You do not need to be an Einstein to realize that this is all about extorting money from you for a decryption key. The problem is that there is no guarantee that you will get this key even if you pay the quite high ransom fee. You should really consider if your files are worth that much at all. Another thing to think about is whether these criminals will send you the key and the decryption tool. We believe that in this case your only hope for recovering your files is to have a recently made backup copy on an external HDD or USB flash drive. If you want to use your computer safely, we advise you to remove CryptoRoger Ransomware from your system immediately.
This ransomware can be called a typical one in the sense that it uses the most common method of distribution – spam e-mails. In fact, this malware infection travels as a fake file attachment that is indeed an executable malicious file. It can be disguised as a document (invoice, online order form, etc.), image, or video. This spam may trick your spam filter and end up in your inbox. Since such mails can be very deceiving, you may feel like you need to open them right away as well as download and open the attached file. This is when you actually infect your system with this dangerous threat and in a minute or two it will already be too late to delete CryptoRoger Ransomware; although this is what you still need to do for your own safety.
Therefore, we recommend that you be extra careful with opening e-mails in your inbox. You should only click on the ones that come from reputable sources and you actually expect them. As you can see, downloading and running attachments can be very dangerous and can cost you your files. Of course, apart from being more cautious, it is best to install an anti-malware application that can automatically remove CryptoRoger Ransomware or it can stop this threat before it could touch ground on your machine.
Nevertheless, if this ransomware has managed to infiltrate your system and you activated it as well, it take about one or two minutes for it to encrypt all your personal files with one of the most typical encryption algorithms called AES-256. The decryption key is further encrypted by one of the RSA algorithms, which makes it virtually impossible to decode your files without the generated private key. All the encrypted files get a ".crptrgr" extension. This infection does not copy itself anywhere; it simply operates from the folder where you downloaded it. However, it does create a registry key named "CryptoRoger," three files in your %APPDATA% folder called: "bg.jpeg" – the background image, "files.txt" – the path of all encrypted files and their MD5, and "keys.dat" – an encrypted file. Furthermore, this ransomware also copies an .html file ("!Where_are_my_files!.html") to all the infected folders plus your desktop. This files contains the instructions, i.e., the ransom note.
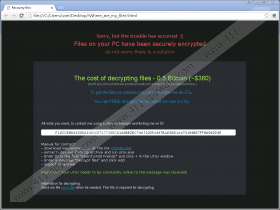
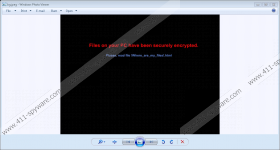
When the encryption is over, this infection changes your desktop background to its own image that is a black screen with red letters saying: “Files on your PC have been securely encrypted.” You are also asked to open the .html file, which you can find on your desktop, for further details. From the ransom note you learn that you have to pay 0.5 Bitcoins, which is around 330 US dollars, in order to get the decryption tool and the private key. You are supposed to contact these crooks via a TOR messaging service called "uTox" for more information about the money transfer. If you send an encrypted file, you can have it decrypted for free so that you can see that these criminals can actually decrypt your files. But we would like to warn you about paying. No, we cannot stop you from doing it, but at least we can tell you that research shows that criminals rarely send the private key or decryption tool. There can be two main reasons for that: one, they do not intend to do so and two, a technical error emerges and the connection between the infection and the server breaks. Although it is possible that the running process deletes CryptoRoger Ransomware itself, there can still remain leftovers. We suggest that you make sure that you remove CryptoRoger Ransomware in its entirety.
The good news is that it is not at all difficult to eliminate this ugly threat from your PC. We have prepared a step-by-step guide for you if you wish to manually delete CryptoRoger Ransomware. Please follow these steps carefully for best results. We believe that there should be no potentially harmful applications on your PC in order for you to be in total security. This ransomware is a major hit but there may be other, less dangerous malware infections as well that can expose you to unsafe web content or cyber criminals. Therefore, we suggest that you use a reliable malware removal program that can save you all the headaches of such malicious attacks.
Remove CryptoRoger Ransomware from windows
- Tap Win+Q and enter regedit. Press the Enter key.
- Delete “HKCU\Software\CryptoRoger” registry key.
- Close the editor.
- Tap Win+E to open File Explorer.
- Bin the malicious executable file you downloaded. (If it is still there.)
- Delete "bg.jpeg," "files.txt," and "keys.dat" from the %APPDATA% folder.
- Bin "!Where_are_my_files!.html" from wherever you can find it.
- Empty your Recycle Bin and reboot your system.
CryptoRoger Ransomware Screenshots: