Bubble Ransomware Removal Guide
Bubble Ransomware is a new malicious threat spreading on the web that can take your most precious files hostage and demand a ransom fee from you for the decryption key. While this may sound shocking to you, let us tell you right now that this ransomware program only looks frightening but there is already a solution out there for you to recover your files. As a matter of fact, we have found that this malicious program is most likely the work of some amateur hacker wannabes. The code itself contains a number of errors that were also discovered by eager malware hunters, who managed to come up with a free decryption tool not long after this dangerous-looking threat hit the web. This obviously means that you do not need to worry about paying the ransom fee or losing your files for a second. But just because there is a way out of this malicious attack, it does not mean that you can leave it on your system. In fact, it is important that you remove Bubble Ransomware as soon as possible because that is what you need to do either you have a backup of your files and would like to transfer them back to your hard disk or if you want to download and use the free decryptor. In the latter case we suggest that you ask a friend or a professional to help you if you are not an experienced computer user. Before we tell you how you can eliminate Bubble Ransomware from your PC, let us tell you more about this vicious program that could have cost you your files.
This ransomware program uses the most frequently used distribution method, i.e., spamming campaigns. Cyber criminals can target lots of unsuspecting computer users with spam and can be very effective. Such a spam can be very misleading and convincing to make sure that you open it. Most of the time it is not even the opening of such a mail that causes the problem, although there are some ransomware programs that can infect you the moment you open the spam. This malware infection mainly infects its victims when the attached file is opened for viewing. How do you get to the point of downloading and running such a dangerous file? Well, quite easily actually. Cyber criminals usually use psychological tricks to make you believe that you are looking at an important and urgent e-mail even if you find it in your spam folder. For example, they can use sender names and e-mail addresses that seem to come from the authorities or any well-know corporation so that you would not doubt the reliability or importance for a second. Then, there is the subject field that can play the largest part in your deception. This can related to matters that everyone would consider rather urgent or at least would feel the need to check the mail out even if the subject did not ring any bells. Such a spam is designed to make you want to see the attached file, which can be disguised as an image or a text document most of the time. Prevention is very important when it comes to ransomware infections because by the time you notice what has happened and you get to delete Bubble Ransomware, your files have already been encrypted and rendered useless.
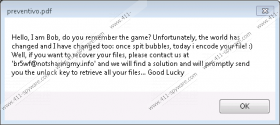
We have no information yet regarding the encryption algorithm used by this threat but we can tell you that it is most likely AES-256, which is the most widely used algorithm built in your Windows operating system. Similarly to most of its predecessors, this ransomware also targets your most important personal files, including your photos, videos, and documents. The affected files get a new extension (".bubble") that makes it easy for you to identify all the encrypted files on your system. When the encryption is done, this infection does not block your main system processes (Task Manager, Registry Editor, and explorer.exe) and it does not replace your desktop background image either. It simply displays a small application window that contains a short ransom note. There is not much information shared; all you learn is that you have to send an e-mail to "br5wf@notsharingmy.info" to get further instructions regarding the payment. This small window cannot be closed unless you launch your Task Manager. Luckily, you are saved this time because even if your files have been encrypted by this amateur ransomware, you can find a free decryption tool online and use it to recover your files after you remove Bubble Ransomware from your system.
In order to eliminate this dangerous threat manually, you need to be able to identify the random-name malicious process in your Task Manager. This process has a characteristic description ("preventivo.pdf") by which you can easily identify it. Once this process is ended, you can delete the related files from your computer. Please follow our instructions below if you feel up to the task of manual removal. If you want to use an automated tool instead, we recommend that you install a trustworthy anti-malware application, such as SpyHunter. Should you need any assistance with the removal of Bubble Ransomware, please leave us a comment below.
How to remove Bubble Ransomware from Windows
- Open the Task Manager by pressing Ctrl+Shift+Esc simultaneously.
- Locate the random-name malicious process.
- Click on the suspicious process with your right mouse button.
- Choose Properties.
- If the Description field shows "preventivo.pdf", check the Location field to be able to find the malicious executable.
- Click OK.
- Click End task while the malicious process is still selected.
- Close your Task Manager.
- Press Win+E to open File Explorer.
- Locate and delete the malicious executable file.
- Locate and delete the file you have downloaded recently from the spam mail.
- Empty your Recycle Bin.
- Reboot your PC.
Bubble Ransomware Screenshots: