Blocking Ransomware Removal Guide
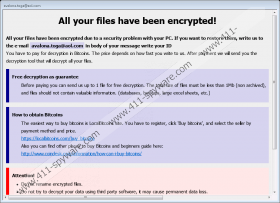
Blocking Ransomware is a malicious application that shows a pop-up window titled as avalona.toga@aol.com or by any other suspicious email address, which claims “All your files have been encrypted!” Sadly, it is most likely true since our researchers confirm the malware can and should lock almost all data available on the user’s computer. If you encountered this threat you might see it for yourself by simply trying to open one of the files on the infected PC; if it cannot be displayed, it means it was affected. At this point, it is important to know the decryption tools guaranteed in the shown ransom note may never be sent even if you pay the requested ransom; thus, if you do not want any more losses we advise you not to take any chances. Another good idea would be to erase Blocking Ransomware from the system, as keeping it on it might cause users trouble later on. Of course, we can help users with this task if you follow our removal steps available below this text.
It is unknown how the malicious application is distributed for sure, but based on all the experience we have with such threats, we would say it was probably spread through infected email attachments, fake updates, or malicious software installers. Consequently, we advise users who encountered Blocking Ransomware to be more careful with data downloaded from the Internet. If it raises even the slightest suspicion, it would be safest to scan it with a reliable antimalware tool first. It should not take long to check the file, and in case it appears to be infected, you might save your computer and all files on it from ruin. So far it does not look like the malware needs to install itself to run on the system. It means the threat can work right from the directory where its launcher was downloaded.
Even though it takes some time for malicious applications like Blocking Ransomware to lock all their targeted data, users rarely notice any changes. While the files are being encrypted, they should be renamed and marked by a particular extension. Instead of the file's name, you should see the malware’s pop-up window’s or in other words its ransom note’s title and the hackers' email address followed by a .blocking extension. The threat is after the user’s videos, images, photographs, other personal files, and program data. The only data it leaves behind are files associated with the computer’s operating system or Internet Explorer. By the time it locks the mentioned files, the malware should display a specific pop-up window. It is opened after launching a file called !#_READ_ME_#!.hta.
With the message inside it (!#_READ_ME_#!.hta ) the hackers should try to convince you that it is safe to pay the ransom. However, we recommend you not to trust them, because if they do not send the decryption tool like they claim they will, you will lose the money you paid as a ransom in vain. If you would not want this to happen, we encourage you not to hesitate anymore and eliminate Blocking Ransomware at once. No need to worry if you do not know where to start since the instructions available below can guide you through the process if you choose to deal with the malicious application manually. Users who prefer removing it with the help of automatic features could install a legitimate antimalware tool instead, perform a system scan with it, then just click the deletion button to get rid of this threat immediately.
Get rid of Blocking Ransomware
- Click Ctrl+Alt+Delete and pick Task Manager.
- Search for a randomly named process associated with the malicious application.
- Choose it and click End Task to stop it.
- Leave the Task Manager.
- Press Windows key+E simultaneously.
- Check the provided locations one by one:
%TEMP%
%USERPROFILE%\desktop
%USERPROFILE%\downloads - Search for the malware’s launcher.
- Right-click the infected file and press Delete.
- Look for the ransom note and eliminate it too.
- Close Explorer.
- Empty Recycle bin.
- Reboot the computer.
Blocking Ransomware Screenshots: