Asasin Ransomware Removal Guide
When Asasin Ransomware slithers in, it is quick to encrypt files that are most vulnerable and valued. The infection does that so that the ransom demands made via BMP and HTM files would be taken seriously. Unfortunately, some users might feel backed up into a corner, and they might give in to the demands. What is more unfortunate, however, is that victims are unlikely to get what might be promised to them. Are you thinking about paying the ransom because you are out of options? Well, you certainly need to think if this is what you should do because it is almost a guarantee that your files will remain encrypted. So, what should you do? The bad news is that it is unlikely that you can do anything to decrypt the files that were corrupted. If backups exist, you can delete Asasin Ransomware and then transfer unharmed copies onto the PC. If that is not the case, you still need to focus on the removal of this ransomware.
Do you remember opening a strange email message and clicking a file attached to it? If this had happened not long before the encryption of your files happened, you have your answer in regards to how the malicious Asasin Ransomware got it. While other methods of distribution could be employed to spread this malicious threat, spam emails are likely to be used. This is how Onion3Cry Ransomware, Incanto Ransomware, Hells Ransomware, and most other file-encryptors are likely to be spread as well. Just like most other threats, Asasin Ransomware encrypts personal files because they are the only ones that are irreplaceable; unless backups exist, of course. The files corrupted by this ransomware are also renamed using a combination of a special ID number and random characters. A unique extension, “.asasin”, is added as well to help you recognize the threat that got into your operating system. Although the extension is unique, the infection itself is just a new version of Locky Ransomware.
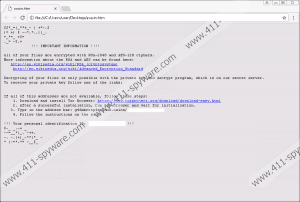
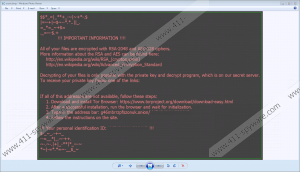
Have you found asasin.bmp and asasin.htm files installed? The BMP file should be represented as your Desktop wallpaper, and the HTM file should be placed on Desktop. Basically, it should be impossible for you to miss the demands that the creator of Asasin Ransomware has for you. Both files represent the same demands, which include installing the Tor Browser, visiting a certain page, and following the payment instructions. According to our research, a ransom of 0.25 Bitcoin is asked in return of a decryptor that, unfortunately, is unlikely to be provided to you regardless of what you do or how much you pay. The ransom note is created to trick you into paying money, and, unfortunately, cyber criminals have the leverage because they are the only ones who can provide you with a decryption key. That being said, there is no reason for them to keep their promises once they get what they want, which is your money. Hopefully, you have not given in because recovering money, in this case, is impossible.
Why is your operating system not protected against malware? If it were guarded by anti-malware software, you would not need to worry about ransomware or any other kind of malware. Needless to say, we suggest installing it as soon as possible. If you do that right now, this software will automatically remove Asasin Ransomware as well. Another option would be to delete this ransomware manually, but, of course, it is not an option that everyone will be comfortable with or that everyone will be able to handle. In fact, there is just one step that is complicated, and if you can get past it, you should have no trouble deleting Asasin Ransomware yourself. We are talking about the identification of the malicious ransomware executable. Have you downloaded and opened it yourself? In this case, finding it should be easy. You might also use a malware scanner to help you find it. But do NOT go removing random files that look malicious because that is how you create problems, not solve them.
How to delete Asasin Ransomware
- Identify the {unique name} file that represents the launcher of the ransomware.
- Delete the file and then move to the Desktop.
- Delete the ransom note files, asasin.htm and asasin.bmp.
- Go to the trash icon, right-click it, and select Empty Recycle Bin.
- Install a trustworthy malware scanner and perform a full system scan. This step should not be skipped because you want to make sure that your PC is clean before you do anything else.
Asasin Ransomware Screenshots:
Asasin Ransomware technical info for manual removal:
Files Modified/Created on the system:
| # | File Name | File Size (Bytes) | File Hash |
|---|---|---|---|
| 1 | asasin.bmp | 2267098 bytes | MD5: 41bba2ec3b1d1244bc19c14799d5c124 |
| 2 | asasin.htm | 10082 bytes | MD5: 11452730547e76caee781a5f257d6c3b |
| 3 | Locky-Asasin Ransomware.exe | 606208 bytes | MD5: 899ba682505dcbbecaa42f5bbd7ea639 |
Memory Processes Created:
| # | Process Name | Process Filename | Main module size |
|---|---|---|---|
| 1 | Locky-Asasin Ransomware.exe | Locky-Asasin Ransomware.exe | 606208 bytes |

