Globeimposter 2.0 Ransomware Removal Guide
When Globeimposter 2.0 Ransomware slithers into your operating system, it does not take much time to corrupt your files and then introduce you to ridiculous demands. The infection is executed from a file that is downloaded onto the computer either by the victim or without their knowledge. In the first case, the user might be tricked into unleashing the infection by opening a corrupted file. In the other case, a secretly active infection could download the file onto the PC silently. Once the launcher is executed, it should be relocated to %PUBLIC% to cover the tracks. By doing this, the infection might protect itself from removal in case the targeted user realizes that the file is malicious. The infection then contacts a C&C server to retrieve/transfer data. Some of the servers that the ransomware is known to communicate with include 121-psychic-reading.co.uk/rf734rgf, abes-bvba.be/rf734rgf, case-vile-brasov.ro/rf734rgf, and cenresa.es/rf734rgf. There are many others. Once the encryption is complete, you will not recover your files by deleting Globeimposter 2.0 Ransomware. You can save your files only with a special decryptor/decryption key, and you are unlikely to retrieve it.
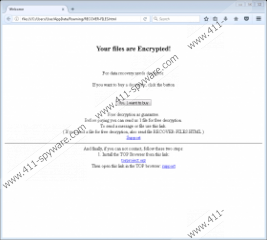
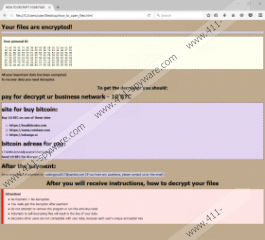
As you can tell by the name, Globeimposter 2.0 Ransomware is the second version of a malicious ransomware. What you might not know is that several different variants of this new version exist. Although both of them work in the same way, and both are removed in the same way too, they are represented in unique ways. First of all, both append different extensions to the files they encrypt. The extensions our research team has recorded included “.725” and “.pizdec”. Furthermore, both versions use different files to introduce victims to the demands. The first version uses a file named “RECOVER-FILES.html”, and the second one uses “how_to_open_files.html”. In the first case, the ransom note is pretty vague as it simply suggests that a decryptor must be purchased. There is no specific information regarding the payment, and the user is asked to send an email to an unknown address. The second version of the Globeimposter 2.0 Ransomware ransom note is much more aggressive as it immediately demands a ransom of 10 Bitcoins to be transferred to 17JW8hLDrnnAiRjcavsrnicUSkFCLFofwK. Unfortunately, it appears that some victims have already made the payments. After doing this, the victim is then asked to confirm the payment by emailing at waitingforyou2017@yandex.com, and that is when the decryptor should become available. Unfortunately, this promise cannot be trusted.
10 Bitcoins is an incredibly large sum that not many ransomware infections dare to demand. Deos Ransomware, SucyLocker Ransomware, Pshcrypt Ransomware, and many other threats might be equally as dangerous, but the ransom fees they demand are hundreds of times smaller. For example, Pshcrypt Ransomware only asks 0.05 BTC, which is still around 200 USD! All in all, whether the ransom is tiny or huge, we do not recommend paying it. Why? Because you are unlikely to get what you need, which, of course, is a decryptor. What are your alternatives? You are unlikely to recover your files using a system restore point because Globeimposter 2.0 Ransomware deletes shadow volume copies using the “vssadmin.exe Delete Shadows /All /Quiet” command. What about legitimate file decryptors? At the time of research, this was not an option either. Does that mean that you need to pay the ransom for a chance to recover your files? That might be your only option, but, again, paying a ransom is NOT recommended.
You can remove Globeimposter 2.0 Ransomware manually (check out the instructions below), or you can allow a legitimate anti-malware tool to erase this infection automatically. We favor the latter option because by installing anti-malware software you can take care of several problems in one fell swoop. First and foremost, you will have malware erased, and remember that the ransomware might be accompanied by other threats. Secondly, you need to consider your system’s protection, and that, of course, is something anti-malware software is created for in the first place. If you skip this step, you might be facing malware sooner than you think. What about your files? Even if you cannot recover the files corrupted by Globeimposter 2.0 Ransomware, for example, using external backups, you can keep them safe for the future. There’s always a chance – no matter how small – that a decryptor will become available for free. To keep personal data protected in the future ensure that it is backed up.
How to delete Globeimposter 2.0 Ransomware
- Tap Win+E to launch Explorer and then enter %PUBLIC% into the bar at the top.
- Delete the malicious {random name}.exe file representing the launcher of the threat.
- Tap Win+R to launch RUN and then enter regedit.exe to launch Registry Editor.
- Navigate to HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce.
- Delete the value named CertificatesCheck. Its value data should point to the malicious {random name}.exe file.
- Empty Recycle Bin and then run a full system scan to check if you have not overlooked malicious components.
Globeimposter 2.0 Ransomware Screenshots: